The Digital revolution has transformed the world into a “global environment. Here people can easily and quickly converse with each other. In the business world, especially, employees use personal and company-owned mobile devices to do work anywhere. But, a million-dollar issue emerges today. How can we be sure that official information is safe on personal devices and away from the office? The answer is Microsoft Intune, a cloud-based service. This greatly ensures that mobile devices and apps are used safely and under compliance requirements.
Stay tuned with this technical post and learn about Microsoft Intune and its features. Moreover, how it protects information on mobile devices and applications, its benefits, and much more.
Microsoft Intune basics
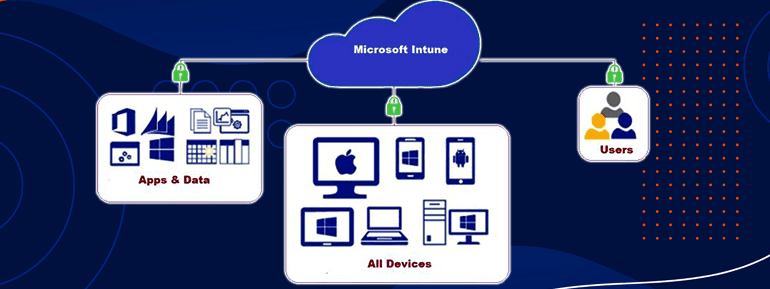
Microsoft Intune is a service that provides Device management (MDM) and Mobile Application Management (MAM) for all digital devices. The devices are mobile phones, tablets, laptops, and other mobile devices. Microsoft Intune supports Windows 10, Windows 11, macOS, Android, and Apple iOS. It is a cloud-based service that gives you complete control over how your organisation’s devices are used daily at work.
The Microsoft Enterprise Mobile + Security (EMS) suite includes Intune. It can work immediately with all Microsoft 365 products, including Azure Active Directory (Azure AD). It gives you control over who and what users can access. Your data is completely safe with Azure Information Protection (AIP) and controlling access.
Why is Microsoft Intune?
Why should we use Microsoft Intune to keep apps and devices safe? Let’s get right to the answer:
- It works on Windows, other platforms, Linux, Android, macOS, and iOS.
- Data belonging to an organisation may be safeguarded and managed remotely using any mobile device, including computers, tablets, and smartphones.
- You could put apps on devices and control availability to them from afar.
- We can structure policies and practices to control the data on the devices with Microsoft Intune.
- You can ensure that both devices and applications follow an organisation’s security policies.
The Overarching Structure of Microsoft Intune
The Microsoft Intune structure contains Azure Active Directory, Office 365, SaaS applications, app marketplaces, application programming interfaces, and more. Microsoft works in tandem with these other services to manage applications and set up devices in a secure manner.
The structure image reference- https://learn.microsoft.com/en-us/mem/intune/fundamentals/high-level-architecture
The function of Microsoft Intune.
Intune enables you to manage applications using specific policies. For example, you can make it so that users can’t access your Office 365 apps unless they’re using a company device, or you can make sure mobile phones follow password policies. Apps like Office 365, Microsoft Teams, and OneDrive can be sent to devices as customised apps.
One great thing about Intune is that it lets users control how they access company data on their own devices. This keeps company data safe and separate from personal information.

When you use Intune, you can do a lot of different things.
How to Use Microsoft Intune:
Most of the time, this is how people use Intune:
- Securing your email and data on-premises so that devices can safely access it
- Keeping your Microsoft 365 email and data safe so that devices can safely access it
- “Offer your own device” (BYOD) programmes should be available to all employees.
- Give employees company-owned devices like laptops, tablets, and phones.
Key features of Microsoft Intune
With the following features, Microsoft Intune keeps devices and apps safe. Here is a list of them:
- Mobile Device Management (MDM).
- Mobile Application Management (MAM).

1. Mobile Device Management (MDM)
With Microsoft Intune, both company-owned and personal devices are easy to manage. Microsoft Intune enrols devices. Signing up allows you to create VPN connections, set up passwords and PINs, and protect personal and work devices from threats.
But users won’t want Microsoft Intune to control their own devices. Microsoft Intune allows you to access resources for work and personal use. Users can set up MFA rules to protect corporate apps and data.
Microsoft Intune MDM Lifecycle
We only know that every device has a certain amount of time to operate. And the life cycle starts with signing up, continues with setting up and protecting, and ends with retiring.

Enrolling: You may join using a phone, tablet, or PC running Windows, Linux, or anything else. Enrol your devices in Microsoft Intune. It enrols customers’ devices to verify they comply with company rules and settings. Enrolling a device lets administrators see all devices accessing the company’s resources. It enables them to provide consumers with Wi-Fi and VPN certifications. It reports how users and devices follow security regulations.
Configure: Choose device protection policies depending on the work. Then, set up your devices with the functions you require. Configuring also prevents unauthorised access to organisation resources. You may manage PCs using Microsoft Intune client software.
Protect: Today, protecting gadgets against threats is crucial. Microsoft Intune supports Multifactor Authentication (MFA), Windows Hello for business, and Windows security policies. MFA provides an additional degree of protection to resource authentication. Windows Hello is available if a gesture or Windows Hello fails. Microsoft Intune client software provides software updates, endpoint protection, and Windows firewalls to secure PCs.
Retire: Losing, stealing, or replacing a gadget is common. When this happens, you must discard or erase the devices. Doing so will improve the accuracy of organisational data. Taking devices out of device management, resetting them, and wiping all corporate data must be done swiftly.
2. Mobile Application Management (MAM)
Mobile Application Management (MAM) comes to secure both custom and stored apps’ data. MAM allows you to organise apps on both personal and company-owned devices. This lets admins set apps to user devices and groups. Not only that, but they can also assign apps to specific groups. MAM enables apps to be configured with precise settings and updates. It also supports seeing information on how users access applications.
How Microsoft Intune MAM makes Apps protected?
Policies for app protection keep Microsoft Intune apps safe. These rules control how we can use applications. Policies for app protection protect devices that have been registered. Users can use organisational resources if they log in with their organisational credentials. If they use their own login information, they won’t be able to get to organisational resources.
Managed Apps are part of Intune. The Microsoft Intune App SDK is used to wrap these apps. MAM handles the rules for protecting apps. Through Managed Apps, users can get to corporate data. You can stop data from getting out and keep corporate data safe. Managed Apps don’t touch personal data, just enterprise data.
What other Services does Microsoft Intune work with?
Microsoft Intune interacts with other services and perks. Microsoft Intune integrates Azure AD, among others. Like Azure Information Protection, Intune protects data. It works with Microsoft 365.
Let’s talk about each integration one at a time:
- Integration with Microsoft 365: This handles user groups with Microsoft 365. Microsoft 365 can build iOS and macOS groups. You may push policies into these groups by visiting App stores, backing up iCloud, utilising Airdrop, and more.
- Microsoft Azure AD: Microsoft Intune with Azure AD provides restricted access to company resources. Access to SharePoint, emails and other apps is restricted to just the conditionally supported devices.
- Windows Defender: This integration protects Windows client services and controls organisation resources. Windows Defender SmartScreen detects suspicious activity in mobile files and applications. Microsoft Defender for endpoint eliminates mobile security vulnerabilities.
12 Core Features of Microsoft Intune
1. Secure Devices
Microsoft Intune-enrolled phones and apps can access business emails. This setup is secure. App servers provide mobile access to on-premises data. Intune-managed certifications offer VPN or proxy data access. Microsoft Intune’s App Wrapping and App SDK secure lba data.
2. Data Protection
Enforcing the administrator-set regulations regarding device registration and compliance aids in keeping Data secure. It makes no difference whether the information is retrieved from an Exchange server, an Outlook account, OneDrive for Business files, or any other source.
3. Option of Multiple Devices
It makes it possible for employees to enrol, register, and then manage their own devices. It also helps them install corporate apps from the self-service Service Portal onto the device of their preference.
4. Evolved Endpoint Analytics
With integrated endpoint analytics, you can keep track of and improve your organization’s progress toward your goal.
5. Excellency, Manage Office mobile apps
It helps the organisation be as productive as possible by giving employees access to corporate resources.
6. Minimise Infrastructure Requirement
Intune helps get rid of the need to plan, buy, and keep up hardware and infrastructure. Endpoint Management makes it easy to control mobile devices from the Cloud.
7. Reduce return on investment
Use the latest cloud features to help protect users’ privacy and your organisation’s data and assets. This will help you get the most out of your Microsoft 365 integrated solution.
8. Monitor All Devices
It lets you set up alerts to know when any device has a problem. It also has Email notifications that go out when something goes wrong so the right people know immediately.
9. Conditional Access
By using conditional access, you can control which devices and apps can access your data. You can set the conditions to allow those devices to access if it meets them. Such as:
- If a device tries to get business data but doesn’t have an antivirus programme. You can block access until the user meets the requirement.
- You can prevent individuals from using their own devices to get to the data.
10. Supports Multiple Mobile OS
It is compatible with Windows, Linux, Android, iOS, macOS, IPadOS, and Windows Phone devices to manage mobile devices.
11. Creates barrier
The Intune app never integrates employee and customer information. The company can wipe all user data or company information from the device. The method of enrolment has a role.
12. International Presence with 24/7 Support
Every EMS membership comes with access to knowledgeable representatives who are ready around the clock to resolve any difficulties that may occur.
Overall, Microsoft Intune offers a unified way to protect data from mobile devices in an organisation. It separates personal and business information on personal devices. Intune helps control access to organisation apps from mobile devices as well as devices. We’ve concluded that Microsoft Intune makes it possible to create a more mobile workforce without putting resources at risk.
Need an initiate with Microsoft Intune?
Using Microsoft Intune (Windows Autopilot) has a lot of benefits. We, as Microsoft experts, can help you switch to Windows Autopilot and use all of its features. Set up Windows Autopilot now so that Microsoft Intune can help you update your IT.
Schedule a free consultation with one of our Subject Matter Experts who will help you right now.