Let’s discuss Microsoft Endpoint Protection and the Microsoft Defender for Endpoint Portal Walkthrough. This portal is a powerful tool that provides you with valuable information. Access vulnerability reports easily, check out the assets section, and view device details.
You can secure your endpoints with the help of Microsoft Defender for Endpoint. Click on the hyperlink to learn more about the product and the different license assignment options available.
By using the Microsoft 365 Defender portal and exploring Microsoft Endpoint Protection features, you’ll gain the knowledge and skills to manage and secure your organization’s devices effectively. The portal provides comprehensive device details, vulnerability reports, risk score assessments, and asset management capabilities, enabling you to take proactive measures to enhance endpoint security and protect your valuable assets.
Microsoft Defender for Endpoint is a powerful solution that empowers enterprises to effectively defend against attacks, optimize security resources, and continuously strengthen their defence mechanisms. It offers leading endpoint security for various platforms, including Windows, macOS, Linux, Android, iOS, and network devices.
What is Microsoft 365 Defender for Endpoint?
Microsoft 365 Defender is an all-in-one solution that covers a wide range of security areas, offering thorough protection for endpoints, identities, emails, apps, and cloud applications. Microsoft Defender for Endpoint (MDE) is the enterprise endpoint security platform within this unified solution.
What are the Advantages of Microsoft Endpoint Protection?
Let’s delve into the key features of Microsoft Endpoint Protection, an enterprise-grade platform for endpoint security. Here are the notable features of Microsoft 365 Defender for Endpoint.
- Endpoint security platform
- Incident Response and Remediation
- Threat Protection and Detection
- Integration with Microsoft 365 Defender Suite
Microsoft Defender for Endpoint Portal
You are given a user-friendly interface when you reach Security.microsoft.com, which acts as the home page for Microsoft 365 Defender. You can effectively manage and safeguard your company’s digital assets thanks to this unified platform’s power-packed combination of security tools and capabilities.
- You need a legitimate Azure AD user ID and the proper access permissions in order to use the Microsoft 365 Defender portal.
- The information below is available on the Home page.
- Noncompliant
- Secure score
- Malware remediated
[videopack id=”10606″]https://www.techomsystems.com.au/wp-content/uploads/2023/06/e7ada27f-30ac-4ef0-9fa0-082bc673_6750.mp4[/videopack]
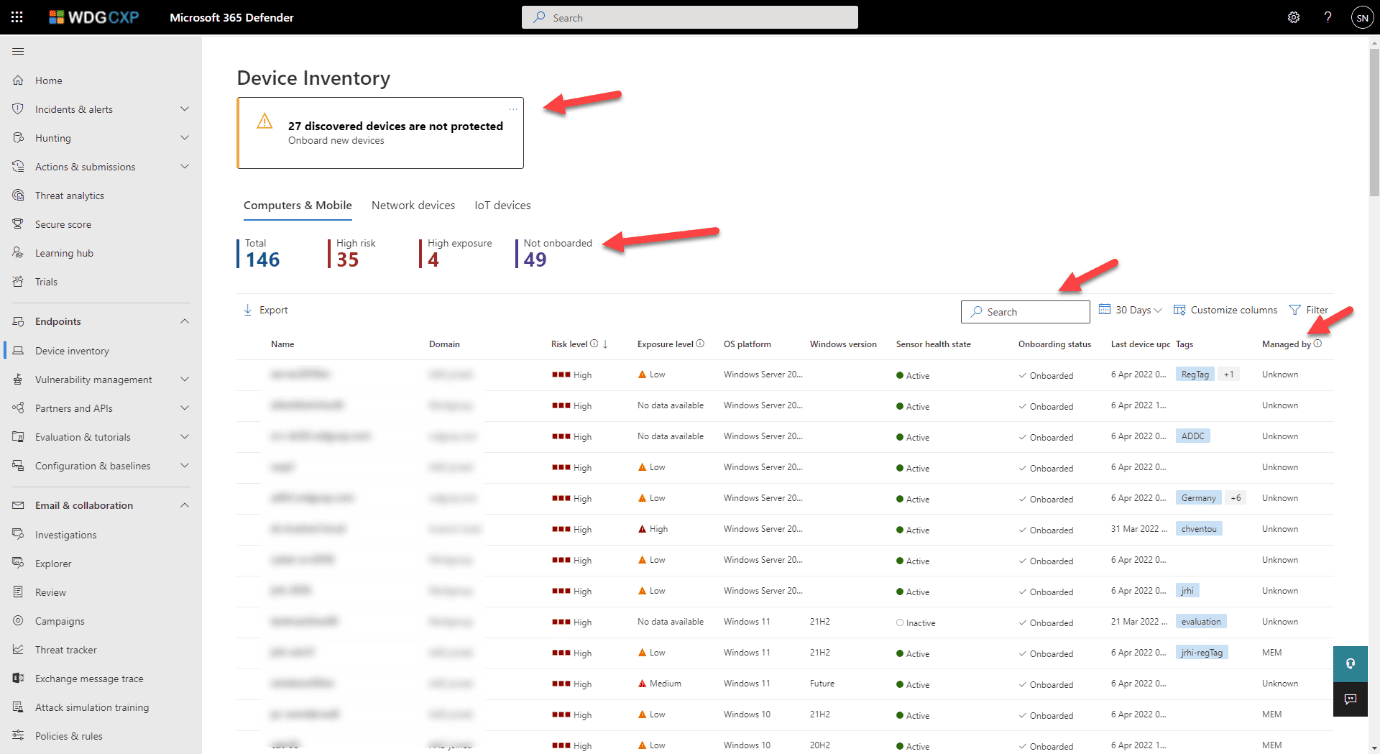
MDE Device Inventory Details
The Device Inventory is shown in the window below.
- Select Assets > Devices.
- You can see the device that we onboarded in the Device tab.
- The onboarded gadget is shown, and the Total number is 1. The onboarded device is an Azure AD joint cloud computer.
MDE Device Properties Walkthrough
Let’s say you choose the device, leading you to study that specific gadget thoroughly. It has menus for Overview, incidents, Alerts, Timeline, security advice, software inventory, found vulnerabilities, and other things.
- Using the overview menu, you may provide Device information such as Domain join type, Windows version, and Intune-managed Onboarding scenarios. You may also view the degree of exposure, people signed in, etc.

You may see certain information in Timeline, such as an SVC host opening an HTTP connection to a specific Windows update site and an SVC host erasing some files. You may see the specifics, including event information, event time, user, entities, etc., by clicking on the black box on the timeline.
Security Recommendation for Windows Devices
There are several security tips in the security recommendation. The 15 security suggestions include things like upgrading Microsoft Edge to the latest Chromium version, activating tamper protection, setting restricted folder access to enable or audit mode, etc.
Software Inventory Choice in Microsoft Endpoint Protection Portal
In order to analyze the CVE, etc., and installed versions, vendor, and Product Code (CPE) data, Microsoft 365 Defender may gather the software inventory details and preserve goods. You can find all of those specifics under the Software Inventory tab.

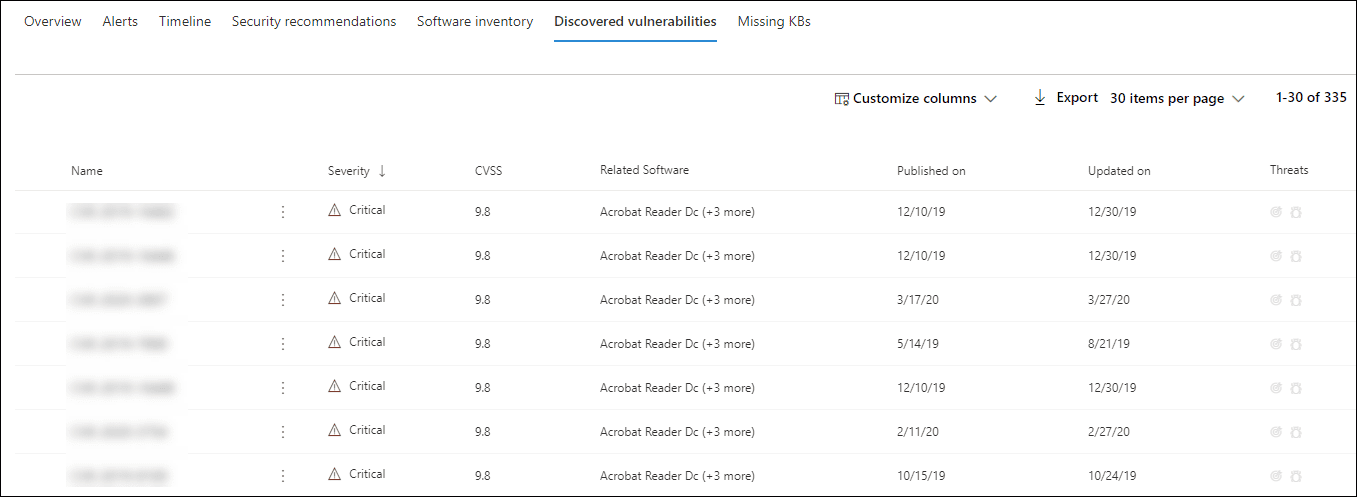
Discovered Vulnerabilities on MDE Portal
Another Important tab is for newly discovered vulnerabilities. The information of the vulnerability, including the date it was published, when it was initially discovered, when it was most recently updated, whether it is a threat, what tags it has, etc., are all shown by Microsoft Defender.
Microsoft Defender Vulnerability Management Dashboard
Defender Vulnerability Management is a powerful tool that provides extensive features to improve the security posture of your business. It offers useful asset visibility, insightful assessments, and potent remediation solutions on various platforms, including Windows, macOS, Linux, Android, iOS, and network devices.
- Vulnerability management contains the following.
- Dashboard
- Recommendations
- Remediation
- Inventories
- Weaknesses

Vulnerability Management Security Recommendations
The security recommendations tab is shown under vulnerability management in the window below. It contains security advice like upgrading Microsoft Edge to use Chromium, encrypting any disks that support Bitlocker, using sophisticated ransomware defence, etc.

Vulnerability Management Remediation
You can locate the Remediation tab in the Vulnerability Management part of Microsoft Defender, which offers a thorough picture of your business’s remediation operations. Exceptions, Blocked Applications, and Activities are the three tabs on this page.

Vulnerability Management Inventories
Microsoft Defender’s Vulnerability Management provides a thorough view of several inventories essential for sustaining a strong security posture in its Inventory section.
| Inventories | Used to |
| Software Inventory | The Software Inventory offers a comprehensive breakdown of the software installed on all of the endpoints in your company. |
| Browser Extensions Inventory | Browser Extensions Inventory helps you to monitor and manage the extensions loaded on your endpoints’ web browsers. |
| Certificates Inventory | Acquire valuable insights into your organization’s endpoint digital certificates with the Certificates Inventory feature. |
| Hardware and Firmware Inventory | The Hardware and Firmware Inventory provides information on the hardware elements, and firmware releases operating on your endpoints. |

Configuration Management Dashboard
The Intune-managed device is number one in Device Configuration Management. MDE, ConfigMgr, and Unknown all score zero. The Device Configuration Management section offers helpful details on the management state of various device kinds within the framework of your company.

Secure your business with Microsoft Endpoint Protection.
In today’s rapidly changing digital landscape, defending your business against threats is paramount. Partnering with TECHOM Systems, a trusted Microsoft Solution Partner, ensures you receive top-notch expertise and comprehensive solutions for Microsoft Endpoint Protection. Our team of experts will guide you through the implementation process, providing strategic guidance, seamless integration, and ongoing support. With us, you can leverage the power of Microsoft Defender for Endpoint services to fortify your business’s security, protect against evolving threats, and achieve peace of mind.
Schedule a call for expert Microsoft Endpoint Protection services and take the next step towards robust protection.