Limiting damage is the fundamental basis of any good cybersecurity plan. This means ensuring that only the best personnel can access businesses’ confidential material and organizational resources. This comes with Azure AD Conditional Access Fundamentals.
This relevant post on TECHOM Systems shows how to set up secure Access in Azure Active Directory and how businesses can use conditional access rules to protect their digital assets beyond essential privilege management.
Azure AD Conditional Access
The Conditional Access Policies are some of the most valuable parts of Azure Active Directory. And you can change the policies to include (or not include) users/groups, apps, and other factors like risk, device web service and status, locations, and application programs (Browser, Mobile, Desktop).
Azure AD Conditional Access is popular and strongly advised to force Multi-Factor Authentication due to the fine-grained assignment controls. But there are a lot of other ways to control Access. MFA is a fantastic way to improve the overall security of your environment by requiring strong user identity authentication. Still, it only applies to the user identity and one part of the Zero Trust model.
When developing preparations, businesses should think about how to identify devices. You can register, join, or hybrid a device’s identity in Azure Active Directory. Using Azure AD Conditional Access, you may need a known and trusted device identity.
Conditional Access can also protect the use of mobile devices with controls for iOS and Android apps that protect data and deny access from using perfect solutions and services.
Currently, there are a few ways to control who gets Access. You can choose one or more and force using a single or all selected options. Among these are:
- Deny Access
- Need more than one way to prove who you are
- Must mark the device as compliant
- The device must be hybrid and joined to Azure AD.
- Mandatory approved availability
- Involve app security plan
- Additional prerequisites (Configurable Governs, Terms of Use) (Custom Controls, Terms of Use)

Deny Access
Conditional access prevents access according to the settings for the policy assignment. Before you turn on a conditional access deployment service,

There are a few things you should think about, including the following:
- !!! Tread cautiously!!! Organizations can be locked out of the Azure portal if they have a Block Access policy that applies to all users and apps.
- From personal experience, this does what it says it does. So, there is no need for any group to show that this idea is accurate.
- Any block access policy should always have at least one exclusion account, like an emergency administrative break glass account.
- Use the Conditional Access report-only mode and the What If tool to test first.
- Policies apply to both user access and access by people in charge. For instance, if you block access to Exchange Online, administrators will not be able to use the Exchange Online Admin Centre or the Exchange Online PowerShell.
- If there is more than one policy, the block access policy comes first.
Various modes of authentication are needed
- Azure MFA is mandated. No third-party MFA provider should use this option. Any MFA besides Azure MFA should use custom functions.
Must mark the device as compliant
- One of two ways to set up a Device-based Conditional Access policy is by marking the device as compliant.
- Microsoft’s Endpoint Manager is a must-have. There must be a compliant device. If the user’s device is not up to code, they will be asked to fix it before logging in.
- Users who still need to sign up for their devices should be able to handle this restriction. This will keep them from getting to anything, including the Intune Portal, where devices can be enrolled. This policy can limit access to Azure AD and Intune administrators and do the same for others.
- Users of the app Company Portal can see what went wrong when they did not follow the rules.
The device must be hybrid and joined to Azure AD.
Device-based conditional access is a second choice. Hybrid Azure AD must be set up on the device. A hybrid Azure AD Joined device is just a device that is joined to a domain and registered to Azure AD with a valid Azure AD user. You can use this control to ensure that only PCs that are part of a domain can access Azure AD apps and data.
If you still need to set up Microsoft Endpoint Manager and compliance policies, this option is at least good enough for the Zero Trust model’s definition of a trusted device. That assumes that all corporate devices have the proper security controls and protections.
Avoid using this control when you have not set up Hybrid Azure AD Join because it can stop all users and administrators from getting in.
Mandatory approved availability
This monitoring only works on mobile devices with iOS and Android. This suggestion does not work with Browser assignment environments and overrides the client app condition for mobile and desktop apps. These approved client applications must be used on every device. Also, devices must first register with Azure AD and use a broker app (Microsoft Authenticator for iOS or Microsoft Company Portal for Android). If it still needs to be installed, the user will be asked to use the conditional access deployment service. This option lets Intune Mobile Application Management be added.
This control’s primary purpose is to ensure that trusted and supported applications, like Outlook, are used to stop Shadow IT. One can use it to set up supported application protection policies to ensure for using those data protection methods (like DLP, encryption, etc.)
Involve app security plan
At the time this was authored, a preview glimpse had been shown. Both this control and the one before it, require approved client apps and need the same things to work. An application protection policy was never implemented to go along with the use of a Require-approved client app. The Require app protection policy control now allows you to use an Intune application protection policy. Preview only works with a small number of apps, like-
- Microsoft Cortana
- Microsoft Planner
- Microsoft OneDrive
- Microsoft Outlook
Additional prerequisites
Terms of Service and conditional access deployment service are two more controls that may show up.
Custom controls send users to a compatible external service to meet authentication needs. This enables done with the help of a third-party MFA provider like Duo or RSA. On the other hand, custom controls have stayed in the preview state. Microsoft will soon replace these controls with an easy-to-use solution that works better with other CA features.
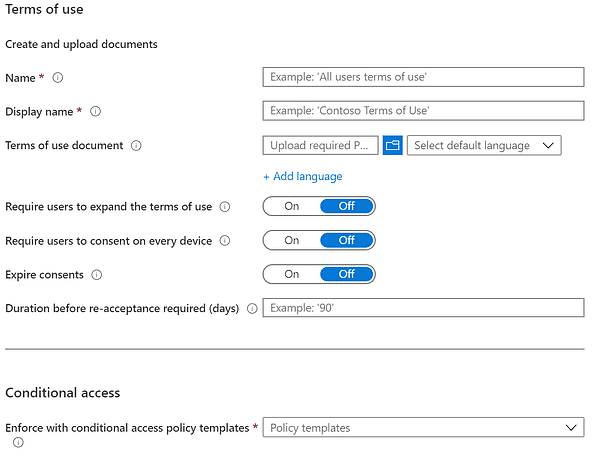
With Azure AD Terms of Use, an organization can give end users information that they must agree to before they can use your cloud services. This can be as simple as a disclaimer or as formal as a document for legal or compliance reasons. Grant controls may show you more options if your organization has made terms of use conditional access rules. With these options, administrators can make users agree to the terms of service before using the resources protected by the policy.
Here are the options for setting up the Terms of Use:
As you can see, you can use many controls to ensure access to your Azure AD environment is safe. Even if Microsoft does not develop the app, conditional access rules become usable with any app associated with Azure AD. If an organization does not already have MFA in place, that should be the first thing they work on to implement organization-wide. But if you already have one or more conditional access policies that require MFA, consider extending your requirements to continue implementing a Zero Trust model to both Microsoft and non-Microsoft applications.
Conclusion
At TECHOM Systems, we are committed to improving how customers use technology and ensuring that IT is aligned with the business correctly. We use the flexibility of on-demand services to solve the problems of collaboration, communication, and security in the modern workplace. We do this by using a Cloud First, Conditional Access, Mobility First approach.
Our professional services team helps our customers set up Microsoft Conditional Access based on different criteria. They do this by following best practices in the industry and making changes based on what our customers need.
Contact our Cloud Computing Consultants and Microsoft solutions experts, who have done this so often that they know all the “strategies” to avoid making errors.
Questions about Azure conditional access can be sent to us through email at hello@techomsystems.com.au or enquire by dialing +61 3 9005 6868. We have specialists available to help you around the clock.