In this growing digital era, ensuring robust endpoint security has become more critical than ever before. With the proliferation of sophisticated cyber threats, organisations need comprehensive solutions beyond traditional antivirus protection. Microsoft Defender for Endpoint emerges as a formidable ally in this battle, offering a suite of advanced features designed to detect, respond to, and mitigate a wide range of security threats.
Understanding Microsoft Defender for Endpoint
Formerly known as Microsoft Defender Advanced Threat Protection (MDATP), Microsoft Defender for Endpoint is an integral component of Microsoft’s comprehensive security ecosystem. It provides organisations with a holistic approach to endpoint security, combining proactive threat detection, automated response capabilities, and insightful reporting features.
Onboarding Computers with Microsoft Defender for Endpoint
Onboarding computers with Microsoft Defender for Endpoint is a straightforward process that can be seamlessly integrated into your existing infrastructure. By leveraging the capabilities of Microsoft Endpoint Manager and Microsoft Endpoint Configuration Manager, organisations can efficiently deploy and configure Defender for Endpoint across their network of devices.
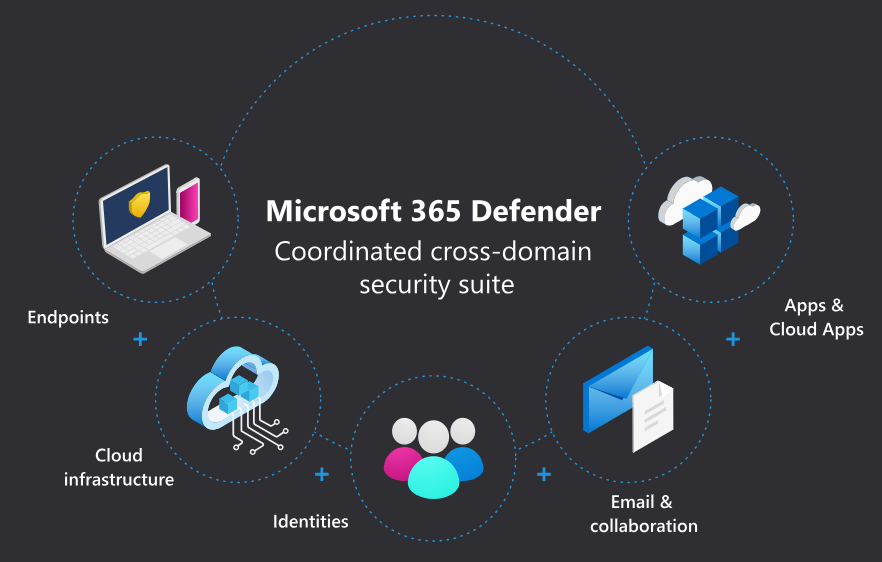
Integration with Microsoft 365 Services
Microsoft Defender for Endpoint seamlessly integrates with various services within the Microsoft 365 suite, ensuring comprehensive threat protection across multiple fronts. These integrations include:
- Microsoft Endpoint Manager: Offering multi-strategy threat detection and response capabilities.
- Intune: Providing traditional cloud-based Mobile Device Management (MDM) and Mobile Application Management (MAM) solutions.
- Desktop Analytics: Facilitating log analysis to identify potential security risks.
- Autopilot and More: Enabling automated setup and pre-configuration of devices for enhanced security posture.
Coverage Expansion and Onboarding Options
Over the years, Microsoft Defender for Endpoint has expanded its coverage to support a wide range of operating systems. From Windows to macOS, Linux, iOS, and Android, organisations can leverage Defender for Endpoint to secure their diverse fleet of devices.
Onboarding Methods for Windows Operating Systems
For Windows-based operating systems, Microsoft offers multiple onboarding methods tailored to different versions and deployment scenarios:
- Windows 7 SP1 and 8.1: Requires the use of Log Analytics/Microsoft Monitoring Agent for installation.
- Windows Server 2012 R2, 2016: Similar installation process involving the Microsoft Monitoring Agent.
- Windows 1803, 2019, and 2022: Provides various deployment options, including local scripts, Group Policy, SCCM, and VDI.
Onboarding Methods for Non-Windows Operating Systems
For non-Windows operating systems such as macOS, Linux, iOS, and Android, Microsoft offers specialised onboarding methods to ensure seamless integration and comprehensive protection:
- macOS: Installation can be performed via Intune, JAMF, or BASH scripts.
- Linux Server: Utilises BASH scripts for deployment.
- iOS: Supports onboarding via Microsoft Intune for both supervised and unsupervised devices.
- Android: Offers integration with legacy Device Administrator or Android Enterprise mode via Microsoft Intune.
Accessing Onboarding Resources
All the necessary scripts and information for onboarding devices with Microsoft Defender for Endpoint can be found in the onboarding settings section of the Microsoft Defender Security Center. Organisations can access these resources alongside other management tools at Microsoft Defender Security Center.
Microsoft Defender for Endpoint is a powerful and universal solution for organisations seeking to enhance their endpoint security posture. With its seamless integration with Microsoft 365 services, comprehensive coverage across multiple operating systems, and flexible onboarding options, Defender for Endpoint empowers organisations to detect, respond to, and mitigate security threats effectively and proactively. Partnering with TECHOM Systems ensures that your deployment of Microsoft Defender for Endpoint is seamless and optimised for your organisation’s specific needs, providing expert guidance and support at every step.
Schedule a Free Consultation with our representative today!
Learn more about onboarding Microsoft Defender for Endpoint and how TECHOM Systems can help tailor a solution to meet your organisation’s unique requirements.













