Every device connected to a business network is a potential entry point for attackers. From laptops and desktops to mobile devices, each endpoint can expose critical data if not properly protected. That is why organizations running Windows 10 must look beyond traditional antivirus solutions and adopt advanced security tools. Microsoft endpoint protection for Windows 10 delivers exactly that, offering a comprehensive defense system against modern threats such as ransomware, phishing and zero-day exploits.
With the expertise of TECHOM Systems, businesses can deploy and manage endpoint protection that not only secures their infrastructure but also aligns with compliance standards and long term IT strategies. This blog takes a closer look at how Microsoft endpoint protection works, its key benefit and how companies can maximize its potential.
Why Businesses Need Endpoint Protection?

Modern enterprises face increasingly complex challenges in securing digital assets. Here are some reasons why Microsoft endpoint protection for Windows 10 is crucial:
1. Growing Cyber Threats
Cybercriminals use tactics like ransomware, fileless attacks and phishing to bypass traditional defenses. Endpoints are often the weakest link and without strong security, organizations face data breaches, financial loss and reputational harm.
2. Remote Work Security
With hybrid and remote work, employees connect from multiple devices and networks outside company control. Endpoint protection keeps these devices monitored and secure, maintaining compliance and reducing risks.
3. Regulatory Compliance
Industries such as finance and healthcare must meet strict standards like GDPR and HIPAA. Security tools with encryption, monitoring and reporting help organizations stay compliant, while TECHOM Systems ensures smooth implementation.
4. Business Continuity
Cyber incidents can stop operations and impact revenue. Endpoint protection reduces downtime by detecting threats quickly, isolating compromised devices and supporting rapid recovery to keep services running.
By partnering with TECHOM Systems, businesses can deploy endpoint protection strategies tailored to their operations, helping them stay ahead of emerging risks.
Keep your business safe from cyber threats with Microsoft endpoint protection. Contact TECHOM Systems today for a free consultation.
Benefits Of Microsoft Endpoint Protection For Windows 10

Modern businesses need more than basic antivirus. Microsoft endpoint protection for Windows 10 offers advanced defenses, easier management and greater resilience, helping organizations stay secure while supporting long term growth.
1. Comprehensive Security
Endpoint protection delivers end to end coverage, defending every device connected to the network. It safeguards against malware, ransomware, phishing and other threats by combining real time detection with proactive monitoring. Solutions like Microsoft Defender for business servers further extend this protection to server environments, ensuring that sensitive business data remains secure at all times.
2. Simplified Management
With centralized dashboards, IT teams gain complete visibility into the security status of all devices. Policies can be applied consistently across the organization and threats can be monitored and resolved quickly. This unified approach reduces complexity and makes day to day security management more efficient.
3. Cost-Effective Solution
Instead of investing in multiple standalone tools, businesses benefit from an all in one platform that covers antivirus, threat detection, device control and reporting. This not only reduces licensing costs but also minimizes the overhead of managing different software solutions.
4. Scalable for All Businesses
From small companies with a handful of devices to large enterprises with thousands of endpoints, the solution scales seamlessly. As businesses grow, they can expand protection without disrupting existing infrastructure or investing in entirely new systems.
5. Enhanced Productivity
By reducing downtime caused by cyber incidents, endpoint protection allows employees to focus on their work without constant security concerns. With automated threat detection and faster recovery, businesses maintain continuity and ensure teams remain productive even during potential security events.
Steps to Implement Microsoft Endpoint Protection for Windows 10
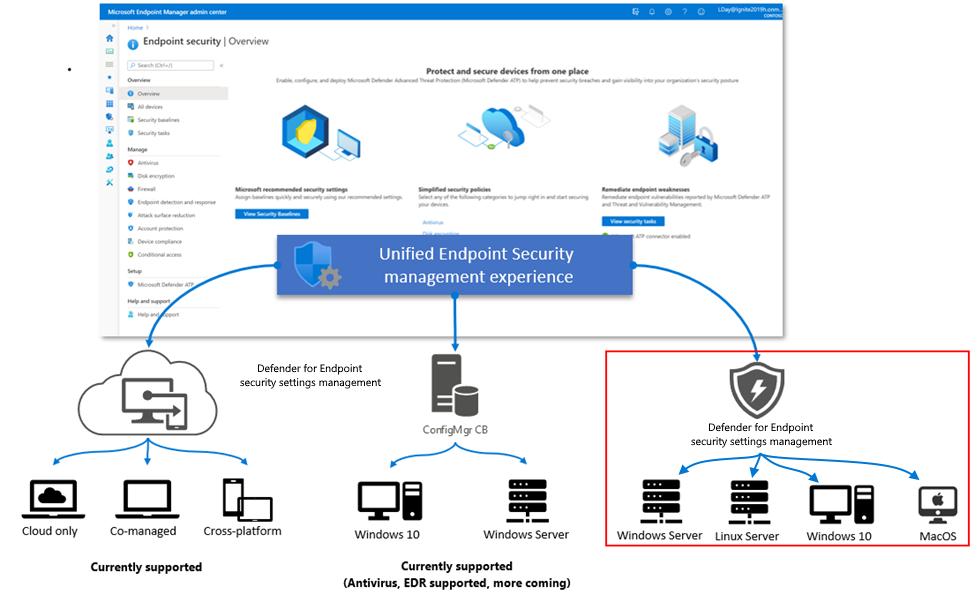
Image Source: Microsoft
Successfully adopting endpoint protection requires a structured approach. Below are the key steps businesses should follow to ensure smooth deployment and maximum security:
Step 1: Assess Current Security Environment
Start by reviewing the existing IT landscape to identify gaps and risks. This includes:
- Listing all devices connected to the network.
- Evaluating current antivirus or security tools in use.
- Identifying outdated systems or unpatched applications.
Step 2: Define Security Policies
Strong protection begins with clear, enforceable rules. Key policies should cover:
- Device usage and access permissions.
- Application control to limit unauthorized software.
- Authentication methods, including multi-factor authentication.
Step 3: Deploy Endpoint Protection
Roll out Microsoft endpoint protection for Windows 10 across the organization. Best practices include:
- Using centralized deployment tools for consistency.
- Applying security baselines to all devices.
- Automating updates and patches to minimize vulnerabilities.
Step 4: Integrate with Other Microsoft Services
Integration strengthens protection and visibility. Businesses should:
- Connect with Azure Active Directory for identity based security.
- Leverage Microsoft Defender for endpoint for advanced threat detection.
- Enable reporting and analytics for real time monitoring.
Step 5: Train Employees
Human error remains a major risk, so employee awareness is essential. Training should focus on:
- Recognizing phishing and social engineering attempts.
- Proper handling of sensitive data.
- Reporting suspicious activities promptly to IT teams.
With support from TECHOM Systems, businesses can follow these steps with confidence, ensuring endpoint protection is effectively deployed and maintained without disrupting operations.
Free Guide For You: The Value of Microsoft Defender for Endpoint
Microsoft Endpoint Protection vs. Traditional Security Software
Many organizations continue to depend on security software for Windows that provides only basic antivirus functions. While such tools can block known viruses or malware, they often lack the sophistication needed to stop advanced cyberattacks. Threats like fileless malware, ransomware-as-a-service and coordinated phishing campaigns can easily bypass outdated defenses, leaving critical business data exposed.
Microsoft endpoint protection for Windows 10, however, goes far beyond standard antivirus. It includes advanced features such as endpoint detection and response (EDR), vulnerability management, automated investigation, integrated threat intelligence and Microsoft endpoint services. These capabilities not only detect attacks but also help prevent, contain and remediate them across all devices. This holistic approach ensures stronger protection against ransomware, phishing schemes, insider risks and zero-day exploits.
With expert support from TECHOM Systems, businesses can transition from relying solely on traditional tools to adopting a security-first model. This shift empowers organizations to proactively address modern cyber challenges, reduce risks and maintain stronger resilience in an increasingly hostile digital environment.
Secure your devices with Microsoft endpoint security. Contact TECHOM Systems today and book a free consultation to strengthen your cybersecurity strategy.
Challenges Businesses Face Without Endpoint Protection
Endpoints are often the first line of defense in a company’s IT environment, yet they are also the most vulnerable. Without effective protection, organizations can face data breaches, operational disruptions and escalating costs. Highlighting these challenges shows why a strong endpoint security strategy is essential:
- Increased Vulnerability to Cyber Attacks- Devices are more prone to malware, ransomware and phishing, increasing the risk of data breaches and financial loss.
- Difficulty Maintaining Compliance- Lack of proper security makes it harder to meet regulations like GDPR and HIPAA, raising the risk of penalties.
- Operational Disruptions- Cyber incidents can halt business processes, reduce productivity and delay projects.
- Poor Visibility and Control- IT teams may struggle to monitor devices and detect threats in real time, leaving networks exposed.
- Increased Costs Over Time- Reactive incident management can be expensive due to remediation, data recovery and legal liabilities.
By implementing Microsoft endpoint protection with support from TECHOM Systems, businesses can overcome these challenges and maintain secure, efficient operations.
Future Of Endpoint Security
As threats continue to evolve, endpoint security must adapt. The future will see more reliance on artificial intelligence, machine learning and automation to detect and prevent attacks faster. Microsoft endpoint protection for Windows 10 is already incorporating these technologies, giving businesses a strong foundation for the years ahead.
By partnering with providers like TECHOM Systems, organizations can ensure they remain proactive and well prepared against future cyber risks.
Choose TECHOM Systems For Microsoft Endpoint Services
Implementing endpoint protection can be complex, but with the expertise of TECHOM Systems, businesses can simplify deployment and maximize value. From licensing guidance to deployment best practices, TECHOM Systems ensures every endpoint is protected using proven Microsoft endpoint protection standards.
Some of the services include:
- Assessment and Planning – Evaluating current IT infrastructure and designing a roadmap for endpoint security.
- Deployment Assistance – Installing and configuring Microsoft endpoint protection to align with business goals.
- Ongoing Monitoring – Providing continuous monitoring and updates to keep defenses strong.
- Training and Support – Educating IT teams and employees to ensure optimal use of the platform.
By working with TECHOM Systems, businesses gain a trusted partner that ensures their endpoint protection strategy is effective and future-ready.
Frequently Asked Questions
#1: What is the endpoint protection service on Windows 10?
Ans: Endpoint protection on Windows 10 is a security service that safeguards devices from malware, ransomware and cyber threats. It combines real time threat detection, automated responses and advanced tools to protect data, applications and network endpoints effectively.
#2: What is MDE in Microsoft?
Ans: MDE or Microsoft Defender for Endpoint, is an enterprise security platform that protects devices from cyber threats. It offers threat detection, automated investigation and response capabilities, helping businesses safeguard Windows, macOS and mobile endpoints.
#3: Is Microsoft Defender an EDR or EPP?
Ans: Microsoft Defender combines both EPP (Endpoint Protection Platform) and EDR (Endpoint Detection and Response) capabilities. It provides real time threat prevention, detection and response, making it a comprehensive solution for securing Windows endpoints.
Conclusion
In this blog, we explored how Microsoft endpoint protection for Windows 10 helps businesses safeguard their devices, data and operations against modern cyber threats. From advanced threat detection and simplified management to scalability and enhanced productivity, the benefits are clear. By partnering with TECHOM Systems, organizations can implement a robust security strategy, ensure compliance and maintain business continuity. Investing in endpoint protection is no longer optional but it is essential for staying resilient in today’s digital landscape.
Protect your business from cyber threats with Microsoft endpoint solutions. Contact TECHOM Systems today and book a free consultation to implement an impactful and effective security strategy.
Paul brings 15+ years of experience designing and stabilizing Technologies, cloud infrastructures and AI-driven solutions. His approach is grounded in curiosity and precision, analysing challenges, breaking them down and implementing solutions that reduce risk and downtime. Known for bringing calm to complex technical situations, Paul helps organizations harness technology efficiently, from cloud migrations to AI deployments. His ability to restore clarity and stability makes him a trusted partner for teams navigating digital transformation. Paul’s mission is to ensure technology is not just functional but strategically empowering.








