Everyone knows that cybersecurity is essential regardless of the size or type of your business. Endpoint security is a big part of that, mainly if your users operate remotely or use mobile devices to access work documents. Microsoft, the best at everything to do with technology, has its own way of protecting endpoints. It’s called Microsoft Defender for Endpoint. If your organization doesn’t already use an endpoint protection tool, here’s one to consider.
What is Microsoft Endpoint Defender?
Microsoft Defender for Endpoint protects end-user devices like tablets, mobiles, laptops, and more, which is good enough for a business. This all-in-one cloud-based endpoint security solution, which used to be called Microsoft Defender Advanced Threat Protection, helps prevent, detect, investigate, and respond to cyberattacks on your organization’s endpoints. Because this solution is in the cloud, there is no need for extra infrastructure or deployment. It also automatically updates, so your endpoints are always protected and up to date.

Security experts stand behind Microsoft Defender for Endpoint, which comes from the deepest threat optics available. In fact, Microsoft employs more than a couple of thousand security experts worldwide to keep you and your data safe. However, Microsoft Defender for Endpoint knows a lot about how to keep computers safe. It can use methods like protection before a breach, detection after a breach, automatic investigation and repair, and more.
This TOS blog has more information about endpoint protection: The Ultimate Endpoint Security Guide: Top Endpoint Security Solutions.
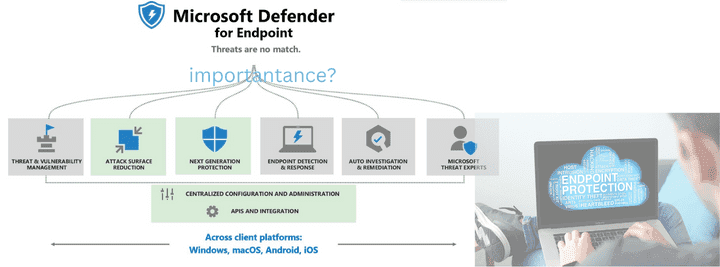
Why is Microsoft Defender important?
Endpoint security for End-point protects the whole device. This solution protects your devices in more ways than traditional anti-virus software and uses preventative protection to lower the risk of a cyberattack. There are five main features that all businesses, no matter how big or small, can benefit from.
1. Taking care of threats and weaknesses
Microsoft Defender for Endpoint will find, rank, and fix misconfigurations in the endpoints in real-time using sensors built into the tool. Using knowledge about how applications are used, Microsoft Defender for Endpoint can first watch the most important assets, such as business-critical applications, sensitive data, and the most critical users. This real-time information can help your IT team handle and protect them better in the future. Knowing how to set priorities can also help the tool make decisions about responding to threats as they happen so that they meet your organization’s needs.
2. Reduces the attack surface
There are areas on your organization’s attack surface where it may be exposed to online threats. There are several ways Microsoft Defender for Endpoint lowers this attack surface area. By plugging security holes, you can lessen the likelihood of an attack by minimizing these surface areas.
Microsoft Defender will first isolate any untrusted documents for the endpoint in a portable container with sensors. The sensors will determine whether or not the manuscript is harmful once it has been opened. If it’s malicious, it will keep your endpoint and network secure by limiting the results to the sandbox and reporting them so your team can see them. Additionally, Microsoft Defender will block access to low-trust websites and use application control to prevent untrusted applications from running.
3. Endpoint Responses and Monitoring
A “presume Microsoft Defender uses breach” approach for the endpoint. This implies that Microsoft Defender examines anything that might seem suspicious. The system will generate an alert that your IT team may look at and handle when a potential danger is identified. Following identification, you can make queries with specially defined actions, set a future alert, or implement the attention and block protocol for similar threats. This tool keeps data for six months so you can spot patterns and determine when an assault started. Thanks to this essential feature, your team has access to recognized potential breaches, which also provides freedom in how they react.
4. Analyzing and fixing issues automatically
Microsoft takes security very seriously and employs more than 3,500 security experts worldwide. This gives them a massive database of algorithms and information used in Microsoft Defender for Endpoint, designed to look at alerts and take action to fix possible security breaches or other security threats. This can make a big difference in how many signs your IT team has to look at and respond to, giving them more time to focus on more complex threats or higher-value projects. Each piece of examined evidence received a verdict: nasty, suspicious, or no danger detected. All these decisions and Microsoft Defender’s actions are kept track of in the Action Centre of the management platform. These decisions and activities can be approved, rejected, or undone if they don’t need to be. With this feature, everything that needs to be investigated or fixed will be done immediately, saving you time.
5. Microsoft Safe Scores for Devices
You will find an overall secure score in the Threat and Vulnerability Management dashboard in the Security Centre. This looks at all the security states, such as the application, operating system, network, accounts, and security controls, and compares them to collected benchmarks and best practices. This gives you a clear picture of your current endpoint security posture, where you should be, and how to improve it. The more your score increases, the more resistant the endpoints are to cyberattacks. In this section, you will also find security recommendations to make your endpoints safer and your overall score.
Minimal requirements for Microsoft Defender for Endpoint
The key criteria for using Microsoft Defender for Endpoint are licensing and software on Windows Server:
Any of the following must be part of the licensing requirements-
- Microsoft Windows 10 E5
- Windows 10 Education A5
- Microsoft 365 E5 which includes Windows 10 Enterprise E5
- Microsoft 365 E5 Security
- Microsoft 365 A5 Security
- Microsoft Defender for Endpoint
Software for Windows Server should indeed get any of the following:
Azure Security Centre with Azure Defender and Defender for Endpoint for Servers (one per covered server)
Also, Microsoft Defender for Endpoint works on most Windows operating systems and servers, including virtual desktops and Android, iOS, Linux, and MacOS. The required browsers are Microsoft Edge and Google Chrome.
Microsoft Defender Pricing for Endpoint
Microsoft sells licenses for Microsoft Defender for Endpoint per user per month. With this license, the user can use up to five devices simultaneously.
Organizations can add Microsoft Defender to any endpoint, whether a Mac, Windows (7, 8, 10) or something else, whether the device belongs to the company or an individual.
Microsoft Defender for Endpoint can be bought in different packages with prices ranging from $10 per user per month to $57 per user per month. These plans can benefit companies with BYOD (Bring Your Device) policies.
Microsoft Defender For Endpoint & Microsoft Defender Antivirus-
The best way to protect and secure the devices in your organization is to use both Microsoft Defender for Endpoint and Microsoft Defender Antivirus. This Antivirus works well with Microsoft Safeguard for Endpoints and is a part of endpoint security for the future. Because the antivirus programs share signals, you get better protection and a more robust single platform. This gives you more helpful information about your security and ways to improve it, like more details and actions for blocked malware.

Your files become secure if your company uses Microsoft Defender for Endpoints and Microsoft Defender Antivirus. This protects your endpoints by giving you a way to back up and restore. It is also recoverable in case of a ransomware attack. Together, these tools will create a shield around your endpoints that will keep them and your network safe from a cybersecurity disaster.
The closing words
Microsoft Defender for Endpoint is an intense and all-around way for organizations of all sizes to protect their endpoints.
At TOS, we implement the Microsoft Defender ATP, an automated system that identifies and neutralizes complex digital assaults on the endpoints of your information technology infrastructure. After thoroughly examining each attack to determine its scope and potential consequences, reports on computer threats will supply. Thanks to the strong tools and automation, you’ll be able to mitigate and eradicate attacks quickly and straightforwardly with the assistance of the Microsoft Defender ATP deployment.
Microsoft Defender ATP is not an antivirus (AV) product, which needs to be said more. We can’t say enough about this.

Get in touch with TOS right away to obtain additional information about Microsoft Defender for Endpoint, and start your risk-free service now.
Contact our professional at +61 3 9005 6868 or mail them at hello@techomsystems.com.au without hesitation.

A results-driven content strategist and IT writer with over 7 years of experience simplifying complex tech concepts into clear, actionable insights. Specialising in cloud computing, cybersecurity, and enterprise IT trends, he crafts content that bridges the gap between technical depth and business value.