Imagine a doctor in a busy hospital using his tablet to review patient records before rounds. He quickly moves from one ward to another, relying on his device to make decisions. What happens if his device is lost or falls into the wrong hands? Sensitive patient data could be exposed, leading to legal issues, regulatory fines and a loss of patient trust.
Many healthcare organizations face this exact problem because mobile devices are convenient but often not secure. Without proper protections, devices become easy targets for cyber threats, creating stress for staff and risk for patients.
The solution lies in mobile device compliance for healthcare. By following proper compliance standards, hospitals and clinics can ensure that patient data remains secure, devices are managed effectively and healthcare staff can focus on delivering care without any disruptions.
Are you confident your hospital’s mobile devices are fully protected? Don’t wait for a breach to find out. Book a free consultation with our experts today and discover how to secure patient data, streamline device management and stay fully compliant with healthcare regulations.
Why Mobile Device Compliance Is Critical For Healthcare?
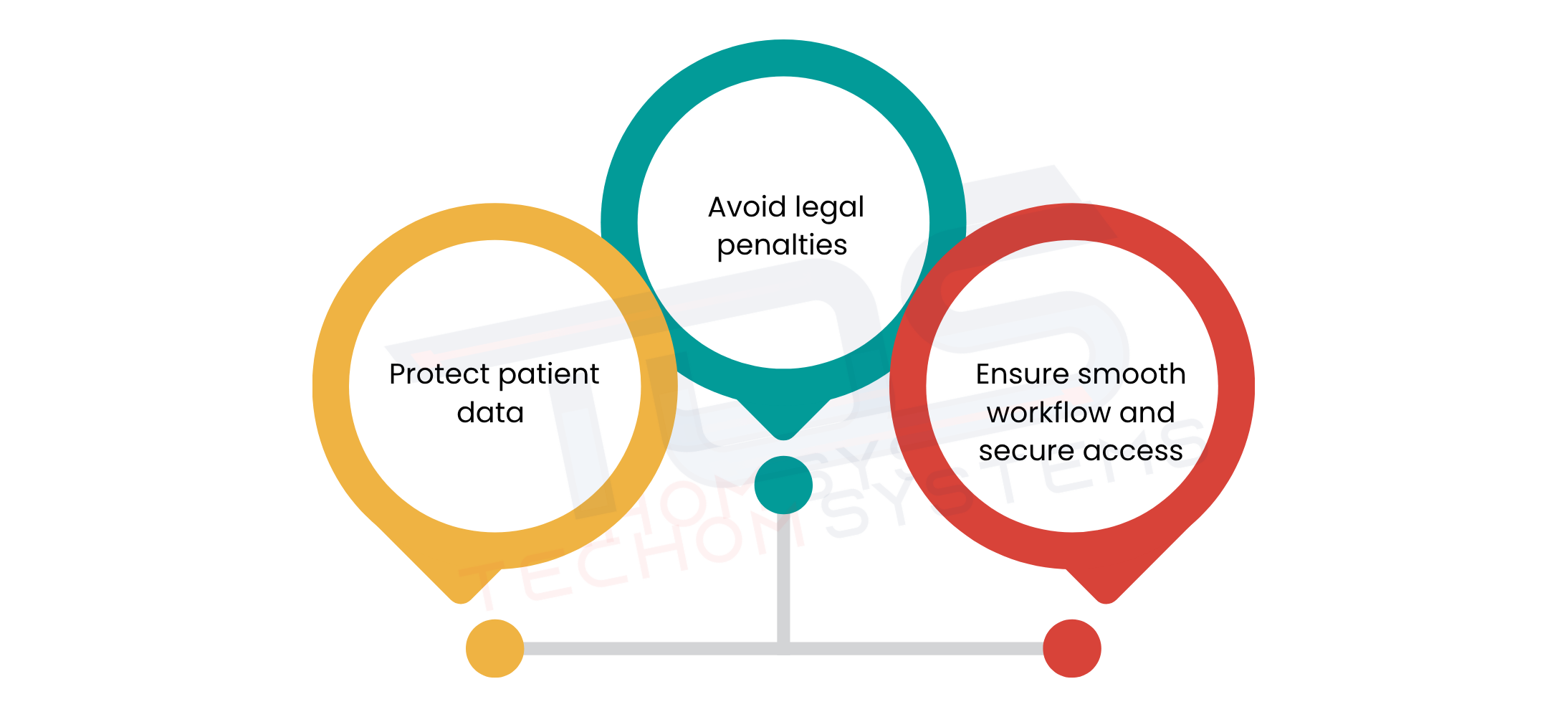
Healthcare providers manage extremely sensitive patient information every day. Without proper security, mobile devices can become an easy target for cyberattacks, data leaks and unauthorized access. Ensuring mobile device compliance for healthcare is essential to protect patient information and maintain trust. Below are the key reasons why compliance matters:
- Protect patient data from leaks or cyberattacks: Hospitals and clinics must safeguard sensitive records to prevent breaches and maintain confidentiality.
- Avoid legal penalties and stay compliant: Following healthcare regulations helps organizations prevent fines and legal complications.
- Ensure smooth workflow and secure access: Compliance allows staff to access patient information safely without slowing down daily operations.
Implementing securing patient data on mobile devices helps healthcare organizations maintain trust with their patients while operating efficiently, reducing the risk of breaches or penalties.
Free Guide For You: Step By Step Guide To IoT Management For Your Business
How To Implement MDM In Healthcare?
Healthcare organizations rely on mobile devices for quick access to patient records and efficient care delivery. Managing these devices securely requires a structured approach. Implementing mobile device management solutions helps maintain mobile device compliance for healthcare and keeps patient data protected. Below are the key steps healthcare organizations can follow to implement MDM effectively and ensure their devices remain secure:
Step 1: Assess Your Device Environment
Start by identifying all mobile devices in use, including hospital owned and BYOD devices. Understand the types of devices, operating systems and how they are currently being used. This assessment helps determine the scope of management and the security measures needed.
Step 2: Define Security Policies
Establish clear rules for device usage, access permissions and data handling. Policies should guide staff on their responsibilities and align all devices with compliance standards. Proper policies reduce the risk of accidental data leaks and ensure consistent security practices.
Step 3: Choose The Right MDM Solution
Select mobile device management solutions that fit your organization’s size, workflow and security requirements. Decide whether a cloud based, on premise or hybrid solution best meets your needs while ensuring scalability and efficiency.
Step 4: Configure Devices and Enforce Security Measures
Set up devices with necessary security settings, including password policies, access restrictions and mobile device encryption in healthcare. Proper configuration ensures sensitive patient information remains secure even if devices are lost or stolen.
Step 5: Train Staff and Monitor Usage
Educate healthcare staff on proper device usage and compliance requirements. Continuously monitor device activity to ensure securing patient data on mobile devices and maintaining mobile device compliance for healthcare.
Step 6: Regularly Review and Update
Periodically audit all devices, update policies and adjust MDM settings to address new security threats and changes in healthcare regulations. Regular reviews keep the compliance framework strong and effective over time.
It is an overview of how healthcare organizations can implement mobile device management solutions to achieve mobile device compliance for healthcare. Following these steps helps protect sensitive patient data, reduce security risks and allow staff to work efficiently without worrying about breaches.
If you want a detailed, tailored plan for your organization, book a free consultation with TECHOM Systems today and learn how to secure patient data effectively.
Key Components Of Mobile Device Compliance
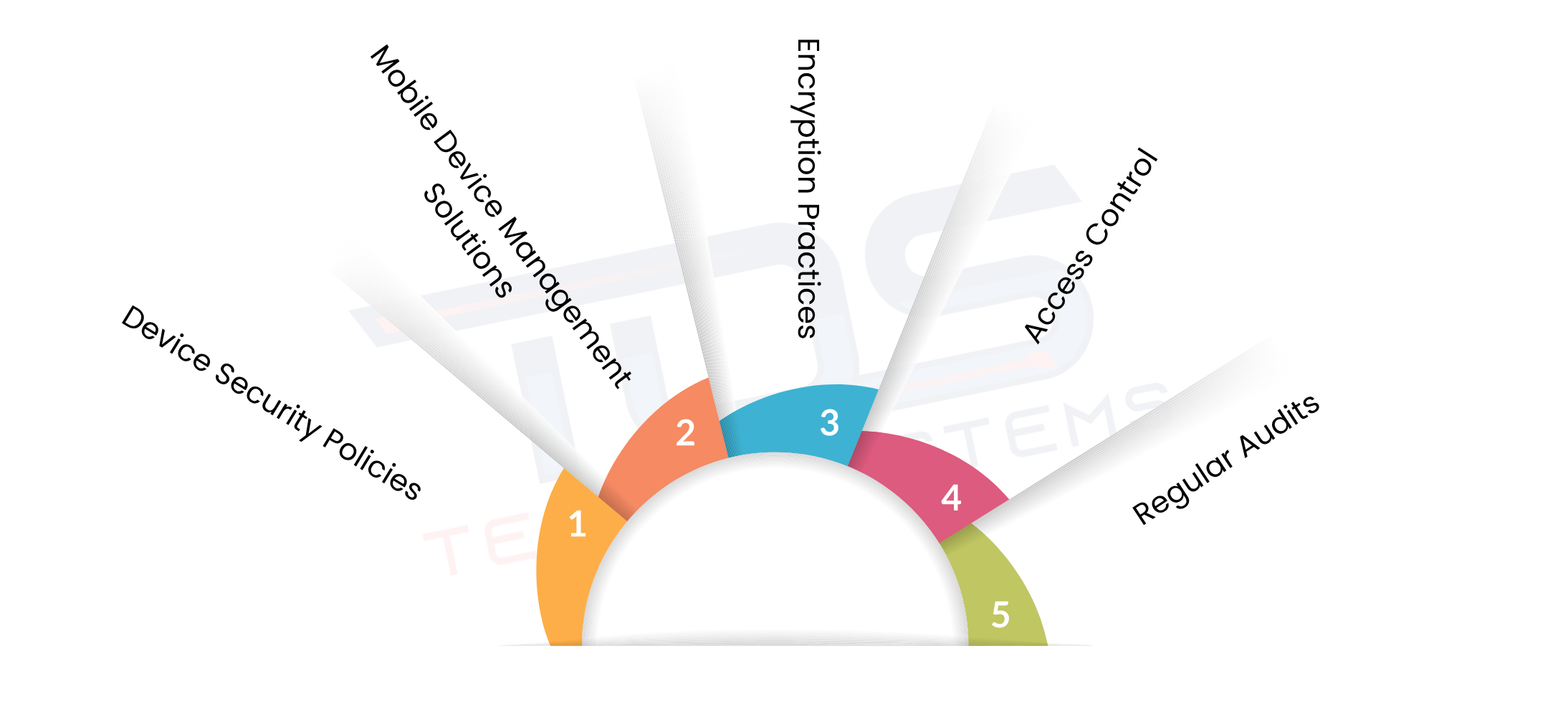
In hospitals and clinics, mobile devices are essential for accessing patient information and managing care efficiently. Because these devices handle highly sensitive data, it is crucial to manage them carefully. Implementing mobile device compliance for healthcare ensures that every device is secure and patient information is protected. Below are the key components:
- Device Security Policies: Set clear rules for all staff, including BYOD devices. Define how devices should be used, what data can be accessed and what security measures must be followed.
- Mobile Device Management Solutions: Use mobile device management solutions to monitor, manage and secure all devices remotely. This ensures devices are configured correctly, updates are applied promptly and compliance standards are maintained.
- Encryption Practices: Implement mobile device encryption in healthcare to protect sensitive patient information. Encryption ensures that data cannot be accessed if a device is lost or stolen.
- Access Control: Restrict access so only authorized personnel can view patient information. This prevents unauthorized access and keeps sensitive data confidential.
- Regular Audits: Conduct periodic checks on all devices to ensure compliance standards are met. Audits help identify vulnerabilities, update security measures and maintain consistent protection for patient data.
Using these practices ensures that mobile devices are secure and patient data is always protected.
Types Of MDM Solutions For Healthcare
Healthcare organizations rely heavily on mobile devices to deliver care efficiently. Implementing the right mobile device management solutions ensures that devices are secure, patient data is protected and mobile device compliance for healthcare is maintained. Below are the types of MDM solutions:
1: Cloud Based MDM
Cloud based MDM allows healthcare IT teams to manage all devices remotely. It is quick to deploy, which is especially useful for hospitals with multiple locations. This type of solution is scalable, so as your organization grows, additional devices can be added without disruption. Cloud based MDM also enables continuous updates and monitoring, helping maintain compliance and reduce security risks.
2: On Premise MDM
On premise MDM gives healthcare organizations full control over their devices and servers. All patient data stays in house, providing enhanced security for sensitive information. Hospitals can customize policies and configurations to match internal protocols and compliance requirements. On premise solutions are ideal for organizations that need direct oversight and stricter control over their mobile environment.
3: Hybrid MDM
Hybrid MDM combines the benefits of cloud and on premise solutions. It provides flexibility by storing critical data locally while running less sensitive operations on the cloud. This approach ensures both security and efficiency. Hybrid solutions also make it easier to manage devices across different departments or multiple hospital branches, maintaining mobile device compliance for healthcare across the organization.
Choosing the right type of solution reduces risks, helps maintain compliance and makes it easier to manage multiple devices across hospitals and clinics.
Free Tips For You: How To Monitor IoT Devices Remotely Effectively
Common Challenges and How To Overcome Them
Implementing mobile device compliance for healthcare is essential, but healthcare organizations often face certain challenges. Understanding these challenges and the right ways to overcome them can make compliance simpler and more effective. The table below highlights common issues and practical solutions:
| Challenge | Description | Solution |
|---|---|---|
| Staff resistance to new security protocols | Healthcare staff may be reluctant to follow new security rules, especially when using personal or BYOD devices | Provide proper staff training, explain the importance of compliance and show how secure practices protect patient data |
| Multiple device types and operating systems | Hospitals often have a mix of smartphones, tablets and other devices running different operating systems, making management difficult | Use effective mobile device management solutions to monitor and secure all devices centrally |
| Ensuring real time monitoring and access control | Without proper monitoring, unauthorized access or data breaches can occur | Continuously monitor devices and enforce access policies to ensure securing patient data on mobile devices |
This table makes it clear how healthcare organizations can address common obstacles while maintaining mobile device compliance for healthcare, keeping devices secure and patient data safe.
Choose TECHOM Systems For Mobile Device Compliance In Healthcare
Healthcare organizations face constant challenges in securing mobile devices and protecting sensitive patient data. Choosing the right partner can make this process simpler, more efficient and fully compliant with regulations. TECHOM Systems offers expert solutions with Hexnode UEM to help healthcare providers achieve mobile device compliance for healthcare while keeping patient data safe. Below are the key reasons to choose TECHOM Systems:
- Expertise in Mobile Device Management Solutions: TECHOM Systems provides tailored mobile device management solutions that fit your organization’s size, workflow and security requirements.
- Focus on Securing Patient Data: The team ensures securing patient data on mobile devices through advanced policies, monitoring and mobile device encryption in healthcare.
- Customized Compliance Strategies: Every healthcare organization is unique. TECHOM Systems creates a compliance plan specific to your devices, staff needs and operational workflows.
- Continuous Support and Monitoring: Beyond implementation, We offer ongoing monitoring and support to maintain compliance and quickly address any security concerns.
By choosing TECHOM Systems, healthcare organizations can confidently manage their mobile devices, maintain mobile device compliance for healthcare and ensure patient information is always secure.
Conclusion
In this blog, we have discussed the importance of mobile device compliance for healthcare and how it helps protect sensitive patient data. We explored the key components of compliance, including setting device security policies, using mobile device management solutions, implementing mobile device encryption in healthcare and controlling access. We also looked at the types of MDM solutions, common challenges organizations face and practical steps to implement MDM effectively.
From this overview, you can see that ensuring mobile device compliance for healthcare is not just about following regulations, but about creating a secure environment where staff can work efficiently and patients can trust that their information is safe. By applying these strategies, healthcare providers can safeguard data, streamline operations and maintain confidence in their mobile device management practices.
Worried About Unsecured Mobile Devices Putting Patient Data At Risk?
Contact TECHOM Systems today and let our experts help you implement mobile device compliance for healthcare to keep sensitive information safe.
A results-driven content strategist and IT writer with over 7 years of experience simplifying complex tech concepts into clear, actionable insights. Specialising in cloud computing, cybersecurity, and enterprise IT trends, he crafts content that bridges the gap between technical depth and business value.







