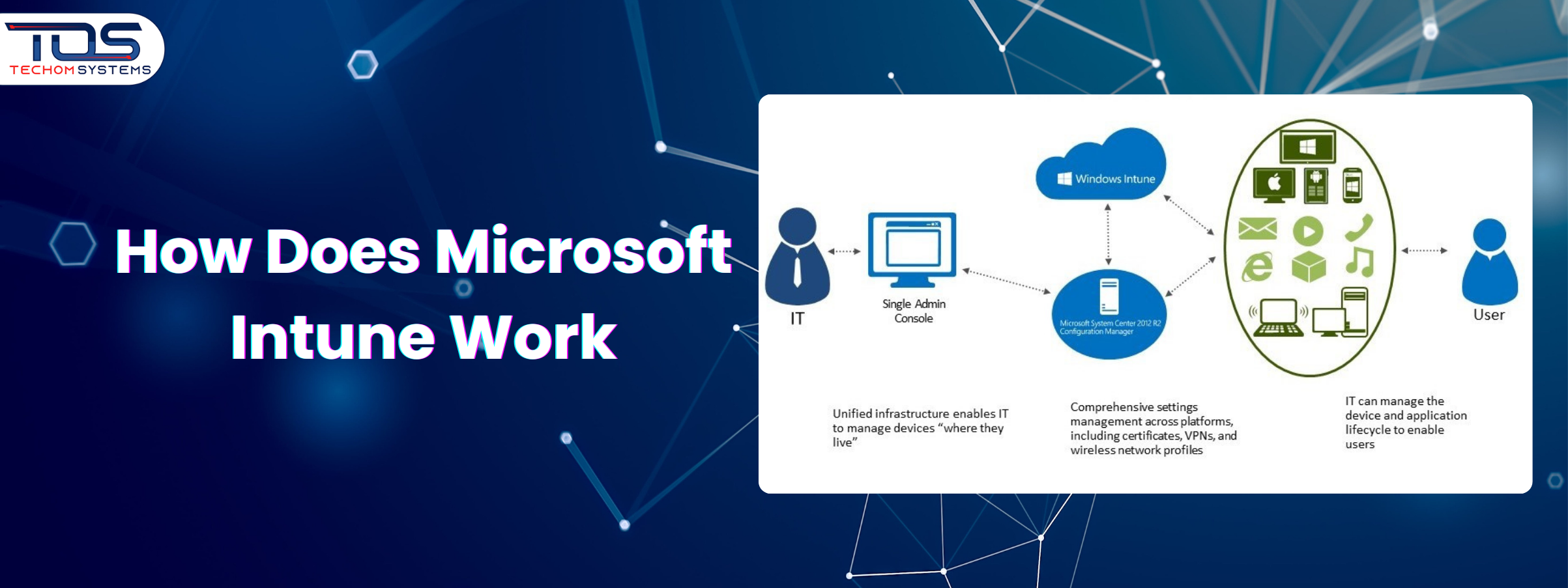
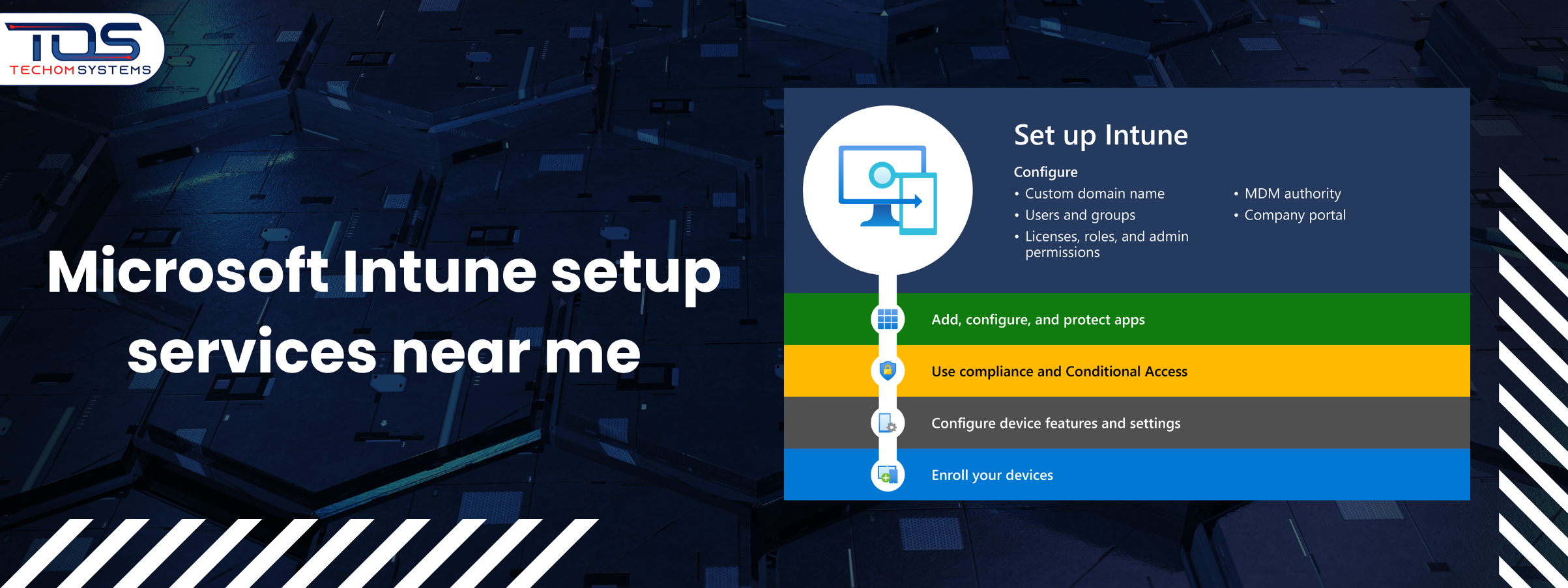
Have you ever asked yourself how does Microsoft Intune work when it comes to managing devices in a modern workplace? IT teams struggle with growing security risks, constant compliance checks and the pressure to keep employees productive on multiple devices. Managing all of this can feel overwhelming without the right solution. Organizations often need a system that simplifies management while keeping data secure.
In this blog we will explain how does Microsoft Intune work in simple terms so you can clearly understand its purpose, the features of Microsoft Intune, the benefits of Microsoft Intune and how it supports endpoint security. By the end, you will also learn how Microsoft Intune deployment services help businesses create a secure digital environment.
To make device management easier, TECHOM Systems can help you implement Microsoft Intune, set up devices, enforce security policies and keep your IT environment running smoothly. Book a free consultation today and find out how Intune can make your device management easy and secure.
How Does Microsoft Intune work?
Microsoft Intune is a cloud based service that allows businesses to manage devices and applications from a single platform. It connects Windows, macOS, iOS and Android devices to the cloud, making management faster, simpler and more secure. By automating device enrollment, configuration and compliance, Intune helps organizations maintain security and productivity across all devices. Here is how Microsoft Intune works step by step to ensure your devices are secure, compliant and ready for business use:
Step 1: Device Registration
The first step is registering the device with Microsoft Intune. This connects the device to the organization’s management system and ensures it is recognized before further configurations. Some important actions in this stage include:
- User registers their device using Intune Company Portal or device settings
- The device is linked to the organization’s directory
- IT administrators can now see and manage the device
Step 2: User Authentication
After registration, the user must confirm their identity using work or school credentials. This prevents unauthorized access. The process usually involves:
- Signing in with Azure Active Directory credentials
- Applying multi-factor authentication for added security
- Allowing only verified users to continue enrollment
Step 3: Compliance Policies Applied
Compliance policies are rules set by the organization to ensure devices meet security standards. At this stage, Intune automatically enforces key requirements such as:
- Password rules including length and complexity
- Encryption settings to protect sensitive data
- Minimum OS version requirements for compatibility
Step 4: Configuration Settings Enforced
To reduce manual setup, Intune pushes network and work-related settings to the device. These settings often cover:
- Secure Wi-Fi profiles for quick connectivity
- VPN configurations for remote access
- Email account setup without manual input
Step 5: Automatic Application Installation
Once policies and settings are applied, the required apps are delivered to the device. Typically this includes:
- Microsoft apps like Outlook, Teams and OneDrive
- Business-specific or custom applications
- Automatic background updates for apps
Step 6: Continuous Monitoring
Device health and compliance are monitored in real time to maintain security and performance. Monitoring involves:
- Regular checks against compliance policies
- Immediate alerts for violations or risks
- Restricting access until issues are resolved
Step 7: Ongoing Updates and Support
To keep devices secure and productive, Intune delivers updates and provides IT support options. The support process includes:
- Automatic delivery of OS and security updates
- Remote troubleshooting by IT administrators
- Reduced downtime and improved device performance
Key Features Of Microsoft Intune
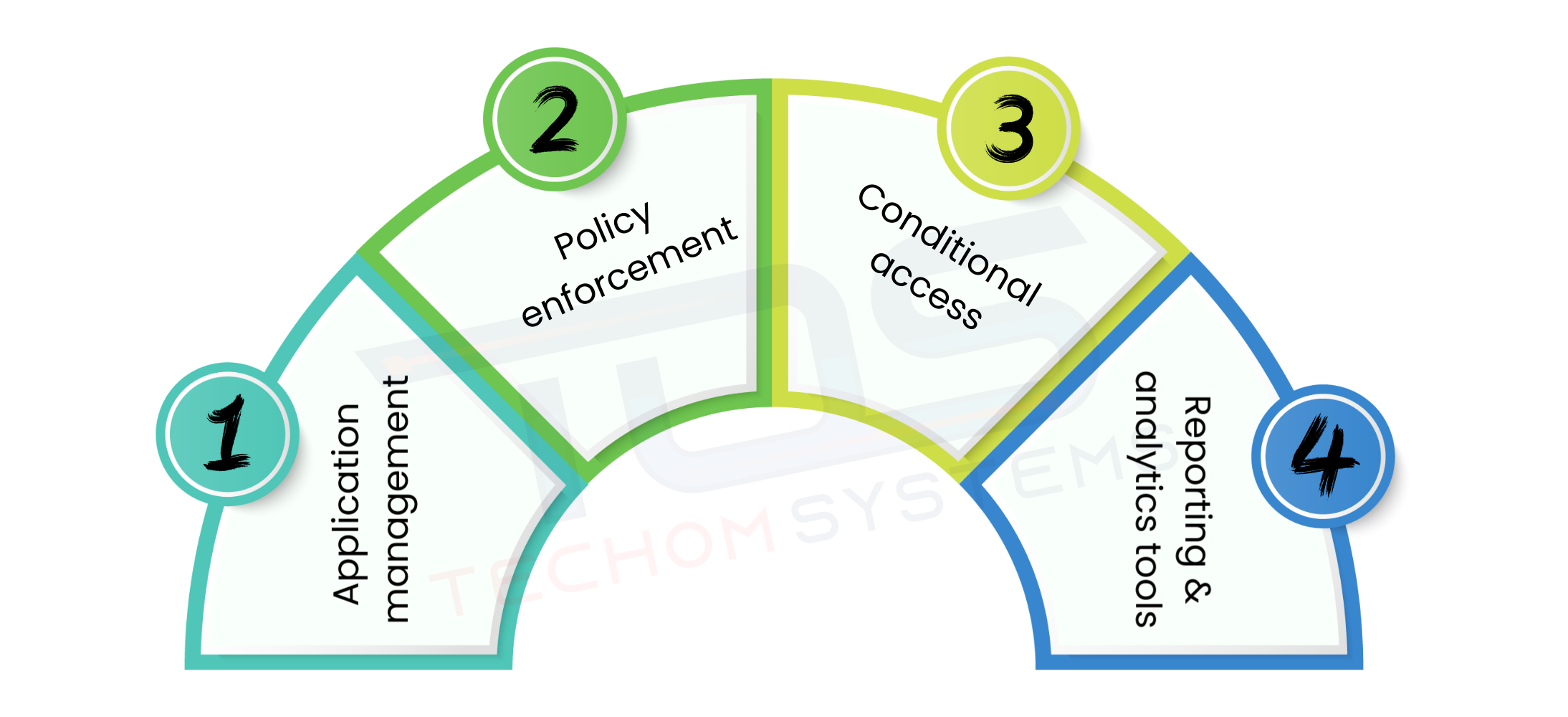
Managing a growing number of devices and applications is one of the biggest challenges businesses face today. With remote work and mobile usage on the rise, organizations need a solution that is flexible, secure and easy to manage. This is where the key features of Microsoft Intune stand out. It brings everything into one platform, reducing complexity for IT teams and ensuring employees have a seamless experience while staying secure. Here are the key features of Microsoft Intune:
1 Application Management
Microsoft Intune allows businesses to control the entire lifecycle of applications. From installation and configuration to updates and removal, administrators decide which apps are allowed and how they are used. This prevents unauthorized apps from creating risks and ensures only business-approved tools are available.
2 Policy Enforcement
Every business has rules for security but applying them manually is not efficient. Intune makes it easier by enforcing compliance policies automatically. This includes setting strong password requirements, applying encryption on devices and ensuring timely system updates. Such measures help protect sensitive data without depending on employees to remember every rule.
3 Conditional Access
Protecting data requires more than just passwords. With conditional access, Intune ensures only trusted users and devices can connect to company resources. For example, if a device is not compliant with security policies, it can be blocked from accessing emails or company apps until the issues are resolved. This approach reduces the risk of unauthorized access.
4 Reporting And Analytics Tools
Keeping track of device health and usage is vital for business continuity. Intune provides detailed reports that show the status of devices, app usage trends and security alerts in real time. This gives IT teams valuable insights to identify problems early and take action before they become serious.
By combining these features, Microsoft Intune becomes more than just a device management tool. It creates a balance between security and productivity, giving employees the freedom to work anywhere while ensuring the business stays protected.
Benefits Of Microsoft Intune For Businesses
Every business today is under pressure to balance productivity with strong security. Managing devices and applications manually often leads to higher costs, wasted time and security gaps. By using Microsoft Intune, businesses can overcome these challenges with a solution that is simple, cloud-based and reliable. Here are the main benefits of Microsoft Intune for businesses:
- Cost efficiency
Microsoft Intune helps reduce the need for expensive physical infrastructure. Since it operates through the cloud, organizations can save money on hardware and maintenance while still keeping their devices and data secure. - Flexibility
Businesses no longer need separate systems to manage personal and corporate devices. Intune offers one unified platform that supports multiple device types, making it easier for employees to work on their preferred devices without compromising security. - Compliance
Meeting industry regulations is a critical part of running a business. Intune simplifies this by enforcing security and compliance policies across all devices. Whether it is password requirements, data protection or software updates, the system ensures consistent standards are applied. - Enhanced security
Protecting sensitive data is one of the biggest concerns for any organization. Intune provides advanced security controls that guard against data leaks and block unauthorized access. This gives business leaders peace of mind knowing that confidential information remains safe.
The benefits of Microsoft Intune extend beyond IT teams. It creates a secure environment where employees can work freely and clients can trust that their information is handled with the highest level of protection.
Want to experience these benefits in your organization? Schedule a call with TECHOM Systems or book a free consultation today to explore the best Microsoft Intune deployment services for your business. Click on the below
How Does Microsoft Intune Strengthen Endpoint Security?
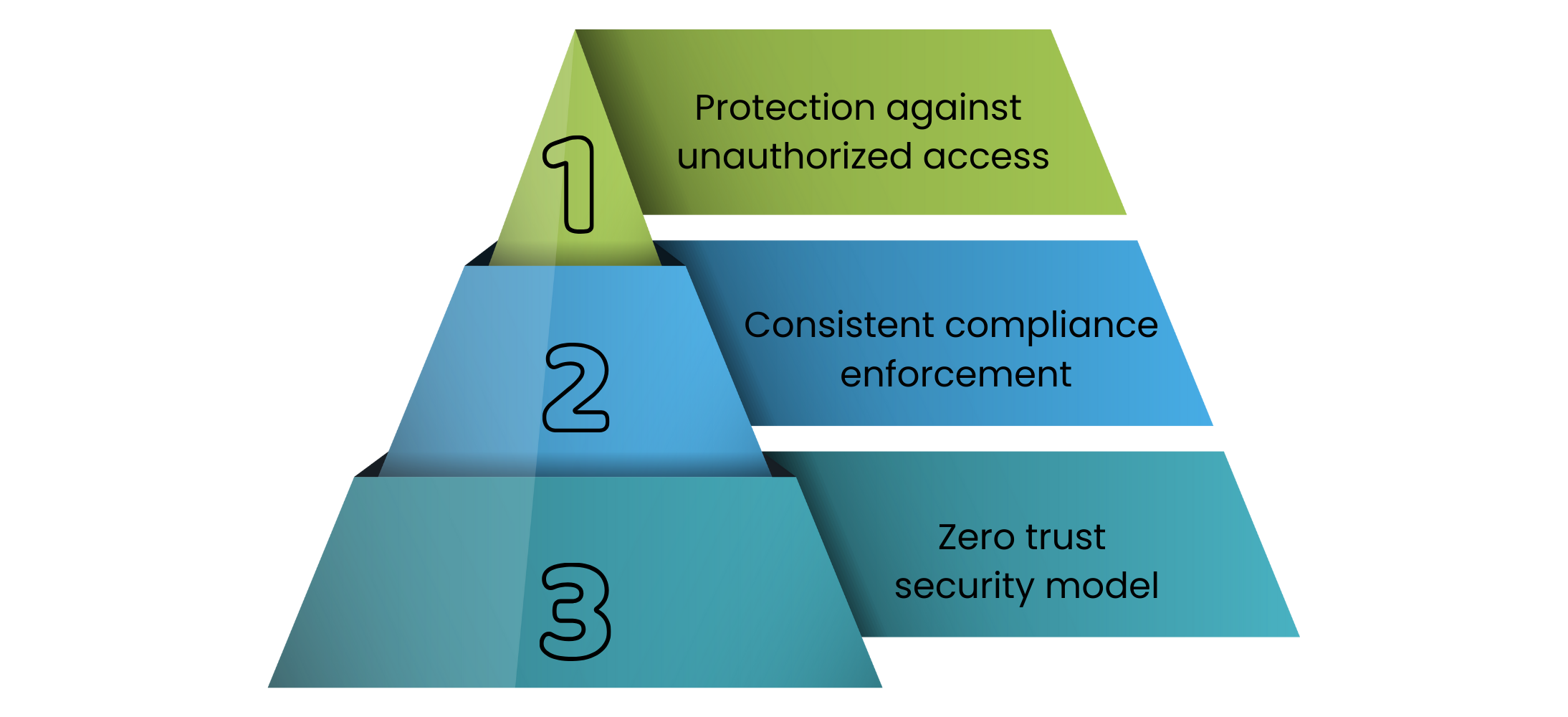
Securing business data has never been more important, especially as companies rely on mobile devices, laptops and cloud applications for daily work. Cyber threats are becoming smarter and businesses need strong protection to keep up. Microsoft Intune Endpoint Security is designed to provide this protection by safeguarding devices, users and sensitive information under one platform. Here are some ways Microsoft Intune endpoint security helps businesses stay secure:
- Protection against unauthorized access
Only approved users and devices can reach business resources, reducing the chances of data leaks or intrusions. - Consistent compliance enforcement
Security rules such as password policies, encryption requirements and update settings can be applied across all endpoints, making sure no device becomes a weak point. - Zero trust security model
Every user and device must prove their trustworthiness before gaining access. This model ensures that even within the network, no one is automatically trusted.
By using Microsoft Intune endpoint security, businesses can build a stronger defense system that adapts to evolving cyber threats while keeping operations smooth and reliable.
Choose TECHOM Systems For Microsoft Intune
When it comes to implementing Microsoft Intune, businesses need more than just technical setup. They need expert guidance, ongoing support and solutions tailored to their unique needs. TECHOM Systems provides complete Microsoft Intune consulting services that make device and application management secure, scalable and reliable. Here is why organizations prefer to partner with TECHOM Systems:
- Expert Microsoft Intune Consulting
Our team offers specialized Microsoft Intune consulting services that help businesses configure policies, manage users and secure devices with confidence. - Seamless Mobile Application Management (MAM)
With MAM, we ensure application-level security by restricting data transfer from corporate apps to personal storage, which is crucial for BYOD environments. - Strong Mobile Device Management (MDM)
We configure Intune with Autopilot deployment, enabling IT teams to manage assets, enforce compliance and secure endpoints with ease. - Advanced Endpoint Security
By integrating Microsoft Intune with Azure Active Directory Security audit and Microsoft Defender, we deliver comprehensive protection through encryption, firewalls and threat detection. - Data Protection at Every Step
Our services include device enrollment, compliance enforcement and policy management, ensuring that business data stays safe across all digital touchpoints. - Scalable and Compliant Policies
We help businesses define, implement and scale Intune policies while maintaining compliance with security standards. - Tailored Security Approach
Whether you need selective data removal or a full device wipe, we offer flexible solutions that align with your organizational requirements.
Ready to secure your devices and simplify management with Microsoft Intune? Book a free consultation with TECHOM Systems today and take the first step toward a safer and more productive workplace.
Frequently Asked Questions
#1: How does Microsoft Intune work And What Is It?
Ans: Microsoft Intune works as a cloud-based service that helps businesses manage devices, applications and security policies from a single platform efficiently.
#2: What Can My Employer See On Microsoft Intune?
Ans: Employers can see device compliance status, installed applications and security settings but not personal files or activity outside corporate apps.
#3: Can Microsoft Intune Track Devices?
Ans: Yes, Microsoft Intune can monitor enrolled devices for compliance, location (if enabled) and security status to protect business data.
#4: What Does Intune Do To Your Computer?
Ans: Intune enforces policies, installs approved apps, applies security settings and monitors compliance to keep company data safe and devices secure.
#5: How Can TECHOM Systems Help With Microsoft Intune?
Ans: TECHOM Systems provides professional Microsoft Intune deployment services, policy management, endpoint security and consulting to keep your business devices protected.
Final Thoughts
In this blog, we have explored how does Microsoft Intune work and why it is essential for modern businesses. We discussed its purpose, the features of Microsoft Intune, the benefits of Microsoft Intune, the Microsoft Intune enrollment process and how Microsoft Intune endpoint security protects your devices and data.
By reading this guide, you now understand how Intune helps organizations manage devices and applications efficiently, enforce compliance, protect sensitive information and improve productivity. You also learned about Microsoft Intune deployment services and how they make onboarding and device management seamless.
If you want to implement Microsoft Intune in your organization and ensure secure, scalable device management, Contact TECHOM Systems for professional guidance and deployment. Book a free consultation today to make your business future ready with Microsoft Intune.

Technical Specialist with 10+ years of experience in IT solutions, data engineering and AI-driven automation. At TECHOM Systems, she focuses on delivering secure, scalable and business aligned technology strategies. She applies advanced technical skills to develop scalable solutions and integrate emerging technologies for optimized digital workflows.