Micro Summary: A consistent IT security audit is mandatory for modern businesses. It is more than a checklist. It is a strategic investment in business continuity. By adopting global information security audit standards (like ISO 27001) and defining a clear information security audit policy, businesses can build a powerful information security audit program. This process reduces risk, ensures regulatory compliance (especially regarding data protection) and is key to strong IT governance.
Key Insights:
- Audit is Not Optional: In Australia, where regulations are tightening, neglecting an IT security audit means risking fines, reputation damage and operational failure.
- Standards are the Foundation: Use globally recognised information security audit standards (like ISO 27001 or the Essential Eight) to give your information security audit program credibility and structure.
- Policy is the Rulebook: A detailed information security audit policy translates the standards into daily, enforceable rules, making your compliance audit manageable.
- Program is Continuous: Security is a cycle. Your audit must be a proactive, scheduled and risk-based audit framework, not a one-off event.
- People Matter Most: The biggest mistake is ignoring the human element. An audit must cover technology, processes and people to address all risk assessment vectors.
Work with TECHOM Systems to create a continuous, standards-based audit program that strengthens your organisation’s security posture.
The Role of Regular IT Security Audits in Risk Management
Australian businesses of all sizes, from local cafes operating online stores to ASX-listed enterprises, are increasingly exposed to cyber threats through the use of technology. As digital systems are embedded into everyday operations, cybersecurity is no longer treated as an IT-only responsibility. Instead, it is recognised as a fundamental business function, positioned alongside finance, governance, and operational management.
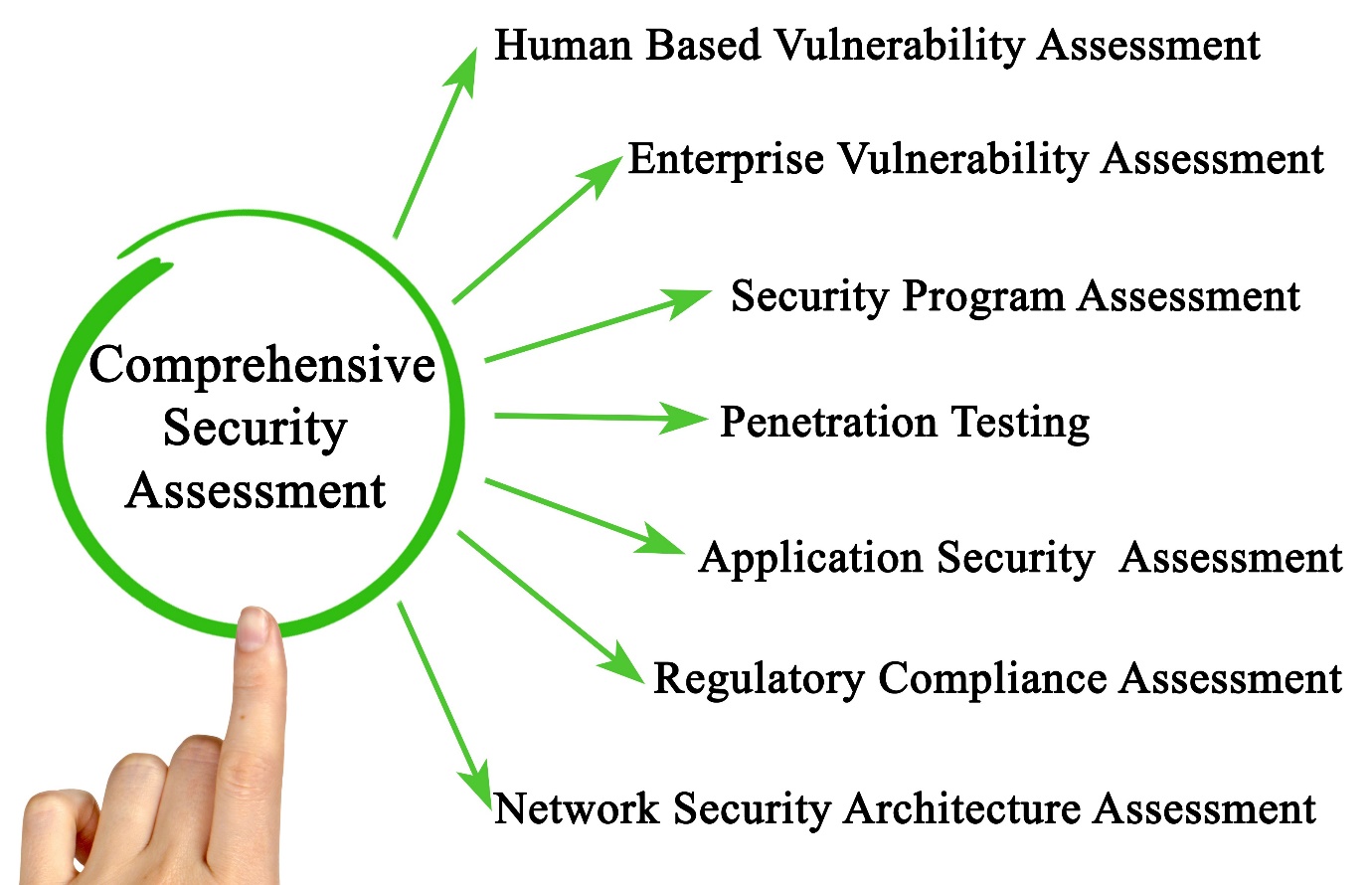
The question is no longer whether a cyber threat will be encountered, but when it will occur and how prepared the organisation will be to respond.
Many organisations invest heavily in firewalls, antivirus solutions, and cloud security platforms, which is a positive step. However, these tools are defensive by nature. Without regular evaluation, it cannot be confirmed that they are functioning as intended or that all potential security gaps have been identified.
This challenge is addressed through a proactive and disciplined process—an IT Security Audit.
This comprehensive guide is intended for Australian decision-makers, IT managers, and compliance officers. It outlines how to move beyond basic security checks and establish a structured information security audit program. The guide also explains the importance of recognised Information Security Audit Standards and a clearly defined Information Security Audit Policy in protecting organisational data and supporting long-term business stability.
The Staggering Risks of Poor Security and Regulatory Non-Compliance
For an Australian business, the consequences of neglecting your cybersecurity best practices are severe and often compounding.

Financial and Reputational Damage
A data breach can cost millions—not just in direct remediation, but in lost business and recovery efforts. Customers lose trust instantly. For a small or medium enterprise, a single, major breach can be catastrophic, leading to immediate closure. A regular IT security audit acts as insurance against this doomsday scenario.
Legal and Regulatory Fines
Australia’s regulatory landscape is tightening, driven by the need for better data protection. Non-compliance with legislation like the Privacy Act 1988 and industry-specific regulations (like APRA’s CPS 234 for financial institutions) carries heavy penalties.
An effective information security audit program is the primary way you demonstrate regulatory compliance to the authorities and stakeholders. This rigorous proof requires adherence to recognised information security audit standards.
Operational Inefficiency and Hidden Costs
Security gaps cause more than breaches; they create friction. Outdated systems, manual controls and confused staff lead to slow operations. A robust audit framework identifies these operational inefficiencies, making your business more secure and more efficient. It’s a dual win for IT governance.
Did You Know?
The financial and reputational stakes of a data breach in Australia are extremely high-
- High Financial Cost: Breaches cost Australian businesses over A$4.5 million per incident on average.
- Prevention vs. Recovery: Proactive auditing is vastly cheaper than breach recovery.
- Reputation Loss: Mandatory reporting under the Privacy Act 1988 instantly magnifies reputational damage.
Don’t risk the $4.5 million cost. Get a robust, risk-focused IT security audit tailored to Australian standards. Secure your business resilience today.
Information Security Audit Standards for Regulatory Alignment
The foundation of any successful IT security audit is the adoption of globally recognised information security audit standards. These standards provide the blueprint for what ‘good’ looks like, ensuring your audit is thorough, repeatable and credible.
What are Information Security Audit Standards?
In short, they are documented requirements that define the policies, procedures and technical controls an organisation must implement to manage information security risks effectively. Using them moves your security from an opinion to a measurable, auditable fact.
Key Standards for Australian Businesses
A few information security audit standards are particularly relevant for businesses operating in Australia:
- ISO/IEC 27001 (and 27002): The gold standard globally. It requires setting up an Information Security Management System (ISMS), which operates on a continuous improvement cycle.
- Essential Eight (ACSC): Developed by the Australian Cyber Security Centre, your IT security audit must include an assessment against this maturity model, which focuses on mitigation strategies to prevent cyber intrusions.
- NIST Cybersecurity Framework: A flexible audit framework widely used in Australia for structured risk assessment and management.
Practical Tips and Benefits of Adopting Standards
- Benchmark Your Position: Standards give you a neutral starting point. You know exactly where your current data protection measures fall short of the industry-accepted best practices.
- Ensure Consistency: By referencing these information security audit standards in your information security policy, you ensure every audit follows the same rigorous process.
- Gain Market Trust: Certification is a powerful signal to customers, partners and regulators that you take data protection seriously—a potent competitive advantage.
An independent audit firm, like TECHOM Systems, specialises in translating complex information security audit standards into actionable steps for Australian businesses, ensuring your compliance audit is efficient and effective.
Establishing an Effective Information Security Audit Policy
The information security audit policy is the internal rulebook that guides every action taken by employees, partners and IT systems related to your data. It defines the what, why and how of your security efforts.
The Critical Role of Your Information Security Audit Policy
Your information security audit policy serves multiple vital functions in maintaining strong IT governance:
- Clarity and Consistency: It eliminates ambiguity regarding rules like password policies and data protection procedures.
- Legal Defence: It is your best evidence of due diligence in the event of an incident or regulatory review.
- Foundation for the Audit Program: It sets the criteria against which your information security audit program is measured.
Steps to Create and Implement an Effective Policy
- Define Scope and Objectives: What systems, data and personnel are covered?
- Conduct a Thorough Risk Assessment: Your policy must directly address the specific threats and risks identified in your risk assessment.
- Draft Specific Control Sections: Translate cybersecurity best practices into rules covering Access Control, Data Classification, Incident Response and Physical Security.
- Enforcement and Communication: The policy must be communicated, taught and consistently enforced.
Common Pitfalls and Solutions
Pitfall | Solution |
|---|---|
| The ‘One-Size-Fits-All’ Policy | Partner with a firm like TECHOM Systems to customise the policy to your industry and audit framework. |
| Lack of Employee Buy-In | Integrate training and explain the why to make the policy easy to access and understand. |
| Infrequent Review | Mandate an annual review and update as part of your information security audit program schedule. |
Developing the Information Security Audit Program
The information security audit program is the engine that drives your continuous security improvement. It’s the strategic plan that schedules, executes and tracks your various audit activities. It moves you from a static security document to a dynamic, risk-adaptive posture.
Definition and Key Components
A robust information security audit program is a cyclical process of planning, execution, reporting and follow-up, designed to assure management that security controls are functioning effectively.
Key components include-
- Scope Definition: Aligning what is audited with the information security audit policy.
- Audit Types: Utilising internal, external and continuous checks (compliance audit).
- Auditor Qualifications: Ensuring the auditors are accredited to assess against specific information security audit standards.
- Risk-Based Scheduling: Prioritising audits based on asset criticality and risk assessment level.
Best Practices for Scheduling, Execution and Documentation
- Scheduling: Prioritise audits based on data sensitivity and key regulatory compliance deadlines.
- Execution: Use both manual interviews (for process review) and automated tools (for technical checking).
- Documentation: Track all findings, assign owners and remediate with clear timelines for effective IT governance.
Benefits Across Business Sizes
- Small Businesses (SMEs): Formalises security efforts using a simple audit framework to meet initial cybersecurity best practices requirements.
- Medium Businesses (MBs): Manages growth and expansion while maintaining regulatory compliance.
- Large Enterprises (LEs): Ensures assurance by providing verifiable proof that complex systems meet stringent information security audit standards.
What Should You Do Now?
Your Information Security Audit Program must adopt a Risk-Adaptive approach for true security:
- Avoid Uniform Auditing: Stop auditing all systems the same way every year.
- Prioritize Critical Assets: Audit sensitive data systems (payments, health) and internet-facing assets more frequently and thoroughly.
- Focus on the Framework: This risk-based model is the difference between compliance and true security.
Upgrade from compliance to resilience. TECHOM Systems provides the expert, risk-adaptive audit framework needed to prioritize fixes and ensure your business is truly secure. Call 1800 867 669 or email hello@techomsystems.com.au to get started today.
The Tangible Benefits of a Proactive IT Security Audit
The value of the IT security audit extends far beyond simply avoiding a breach. It’s a core component of strong IT governance that drives business value.

1. Superior Risk Reduction
A professional risk assessment embedded within an information security audit program prioritises vulnerabilities. You learn where to allocate budget and time where it matters most, proactively reducing your overall threat exposure and achieving effective data protection.
2. Streamlined Regulatory Compliance
A regular compliance audit provides:
- Proof of Control: Verifiable evidence that controls related to information security audit standards are in place and working.
- Audit-Ready Status: The ability to instantly provide reports to regulators.
- Cost Savings: Avoiding hefty fines and legal costs associated with non-compliance.
3. Operational Efficiency
A well-executed IT security audit can enhance efficiency by finding and eliminating redundant systems, correcting over-privileged users and automating high-risk, manual security checks.
Common Mistakes in IT Security Audits
Frequent Errors
- Treating the Audit as a ‘Pass/Fail’ Event: Security is continuous; the audit must be part of the ongoing information security audit program.
- Lack of Scope Definition: Failing to include critical areas like cloud configurations or shadow IT in the risk assessment.
- Ignoring the Human Element: Neglecting staff training and adherence to the information security audit policy.
- Remediation Fatigue: Conducting the audit but failing to implement the recommended fixes.
How TECHOM Systems Helps Prevent Mistakes
- Risk-Focused Scoping: We start with a strategic risk assessment to focus the IT security audit on the assets that matter most.
- Holistic Audit Framework: Our audits integrate technical checks with process reviews and people-audits, aligning with global information security audit standards.
- Remediation Partnership: We provide a prioritised, actionable remediation plan, integrating the required changes back into your long-term information security audit program.
How TECHOM Systems Supports Australian Businesses
TECHOM Systems offers end-to-end IT security audit services tailored to the specific needs of the Australian market, ensuring full alignment with local laws and global information security audit standards.
Overview of Services and Expertise
Our services cover every layer of your security needs-
- IT Security Audits & Risk Assessment: Comprehensive technical and procedural audits.
- Compliance Audit Services: Specialised checks against key regulatory compliance frameworks like ISO 27001 and Essential Eight, providing the expertise to establish an effective information security audit program.
- Policy Development and Review: Crafting a tailored information security audit policy that enhances your data protection strategy.
- Virtual CISO (vCISO) Services: Offering senior-level guidance on IT governance, helping your executive team implement cybersecurity best practices and manage the entire audit framework.
Practical Solutions for Risk Management and Compliance
We turn complex security challenges into clear, manageable projects. By working with TECHOM Systems, you get a partner who understands that your information security audit program is an investment in business continuity and competitive advantage. We provide the expertise to meet stringent regulatory compliance demands while allowing your internal teams to focus on core business operations.
Conclusion
The digital landscape in Australia is more challenging than ever. Every business, regardless of size, must treat its digital assets with the priority they deserve. Implementing a clear information security audit policy, adhering to established information security audit standards and running a disciplined information security audit program is no longer optional, it is essential for survival and growth.
The cost of a breach dwarfs the cost of prevention. A professional IT security audit is the most effective way to gain clarity on your true risk assessment and ensure maximum data protection.
Don’t wait for a regulator’s penalty notice or a hacker’s ransom demand to force your hand. Take control of your IT governance today.
Ready to move beyond reactive security and build a robust, resilient defence?
Contact TECHOM Systems today for a confidential consultation on setting up or optimising your information security audit program. We’ll provide the expertise, the audit framework and the partnership you need to achieve comprehensive regulatory compliance and implement world-class cybersecurity best practices.
Secure your future. Speak to TECHOM Systems now.
A content strategist and IT writer with over 7 Years of experience simplifying complex tech concepts into clear, actionable insights. Specialising in cloud computing, cybersecurity and enterprise IT trends, he crafts content that bridges the gap between technical depth and business value. Helping businesses thrive with practical guidance, Pradeep talks about facts, is keen to share knowledge, and always puts the community first. Outside of work, he enjoys exploring open-source projects and mentoring aspiring IT professionals, reflecting his passion for continuous learning and community growth.








