Summary: As organizations shift toward cloud-first strategies and hybrid work models, Microsoft Intune Architecture and Essentials have become central to modern IT operations. Intune provides a unified, cloud-based platform for managing devices, enforcing security policies and ensuring compliance. The best whether users are in the office or working remotely.
We know that many organizations already invest in Microsoft 365 and what’s often overlooked is that Intune Plan 1 is included in E3 and E5 licenses. This means IT teams can activate powerful endpoint management capabilities without additional costs, streamlining deployment and reducing reliance on standalone MDM solutions.
In this post, I will explain about the core architecture of Microsoft Intune, its essential features for modern workplaces and why its adoption is accelerating.
Prefer to speak with an expert before diving in? Or want to connect with our Intune specialist for a free consultation tailored to your organization’s needs?
What Does Microsoft Intune Do?
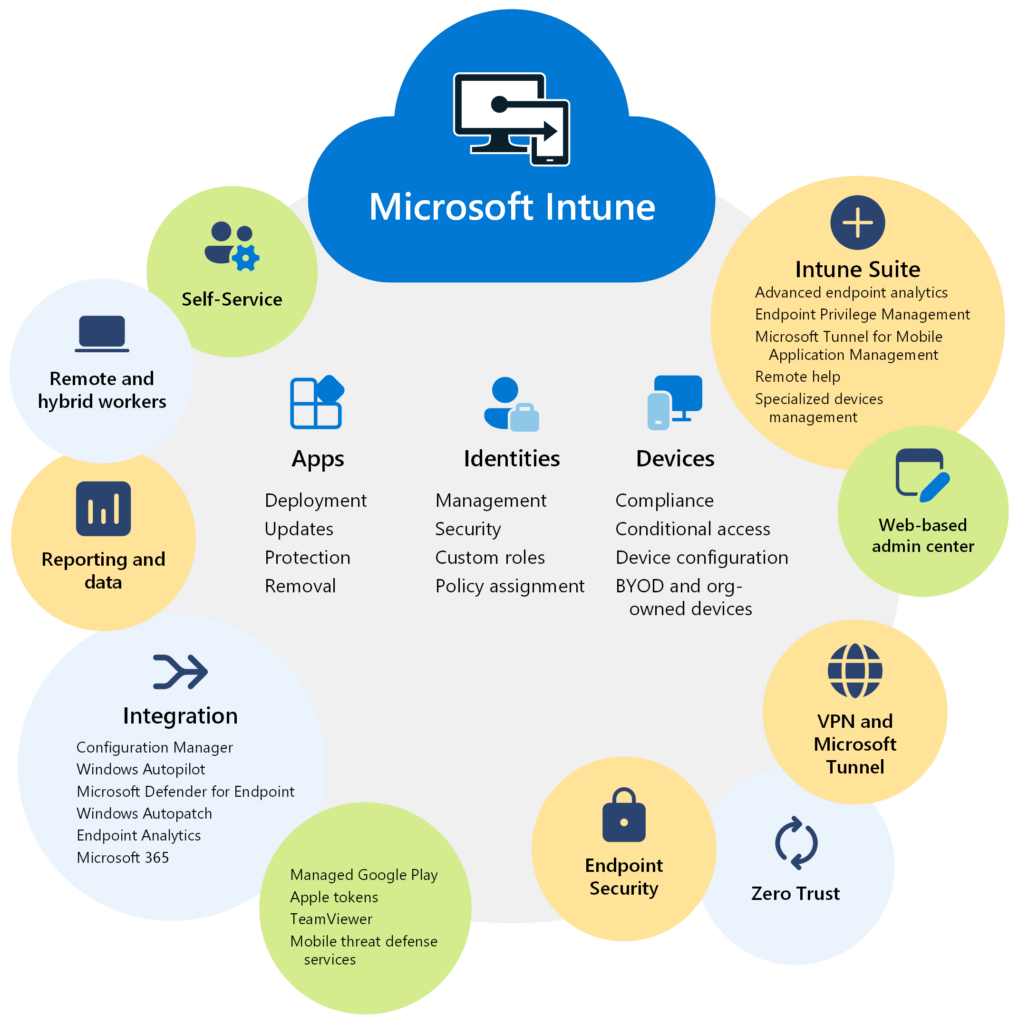
The architecture of Microsoft Intune is designed to support scalable, secure and flexible device and application management across diverse environments, from on-premises to fully remote. It’s built on Microsoft’s cloud infrastructure and tightly integrated with the Microsoft 365 ecosystem, enabling seamless policy enforcement, identity management and security controls.
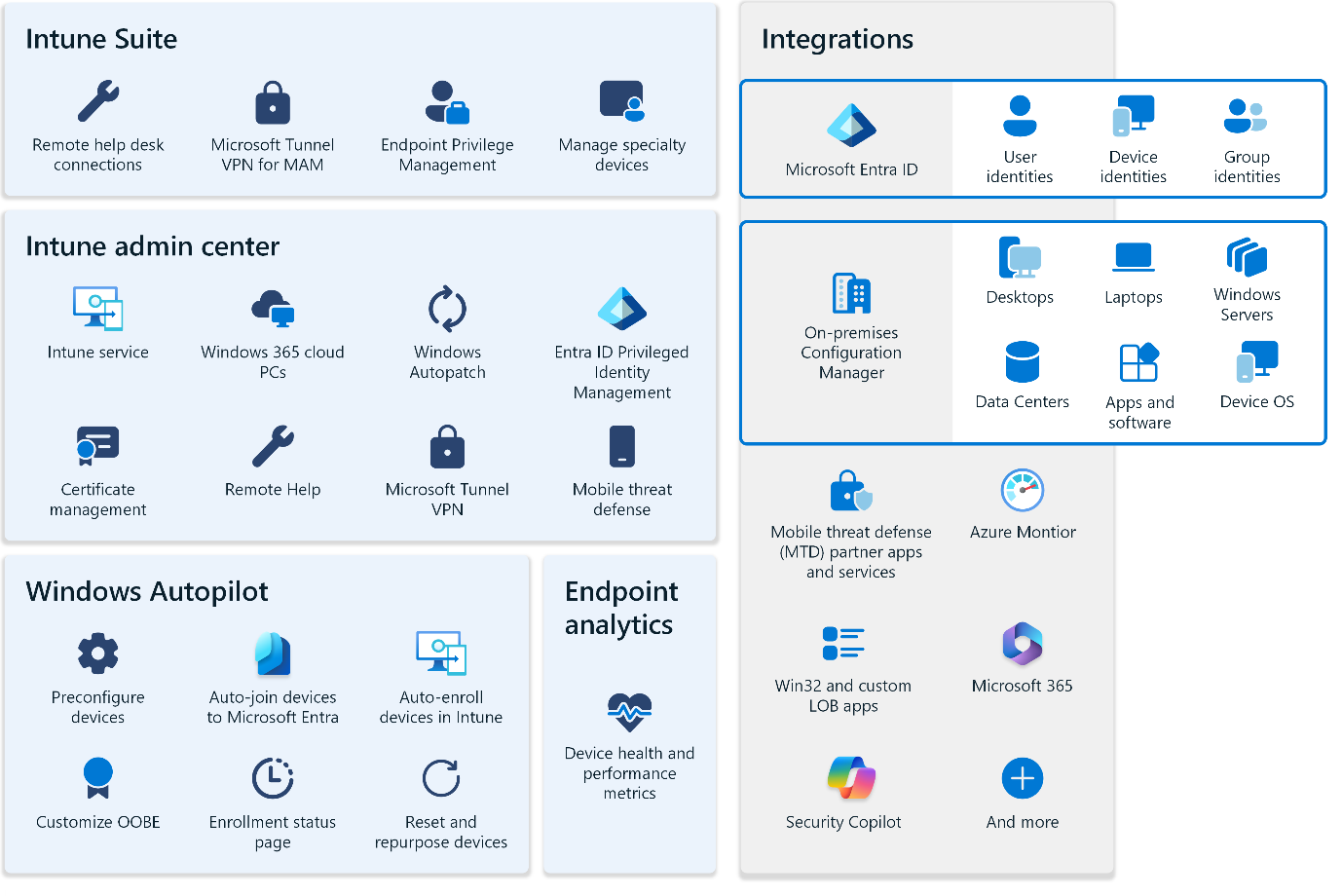
1. Endpoint & Device Management
Microsoft Intune provides comprehensive device lifecycle management across Windows, macOS, iOS and Android platforms.
IT administrators can leverage Microsoft Intune Architecture and Essentials to-
- Enforce device compliance policies such as password strength, encryption and OS version requirements
- Restrict installation of unauthorized or non-business apps
- Automatically configure essential settings like Wi-Fi, VPN and email profiles
- Perform remote wipe or selective data removal on lost, stolen, or decommissioned devices
This ensures that every endpoint accessing corporate resources is secure, compliant and aligned with organizational standards.
2. Mobile Application Management (MAM)
Intune acts as a centralized hub for application deployment and control, ensuring users have access to the right tools while protecting sensitive data.
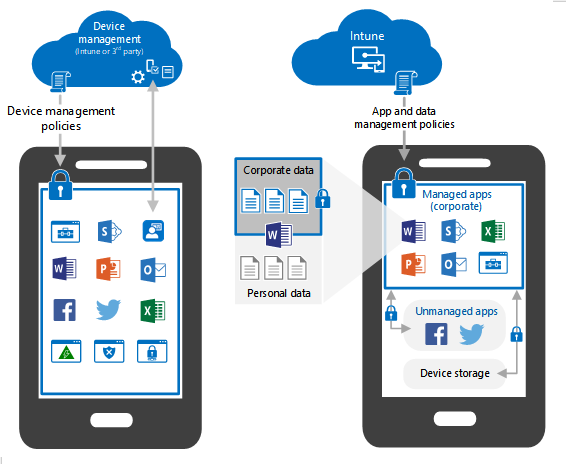
Key capabilities include-
- App deployment across managed devices, Win32, MSI, Store apps and LOB apps
- App protection policies that prevent data leakage from corporate apps
- Automated app updates to maintain security and performance
- Selective wipe of business apps and data when users leave or change roles
A strong grasp of Microsoft Intune Architecture and Essentials enables IT teams to manage apps and devices efficiently, maintaining control without disrupting user productivity.
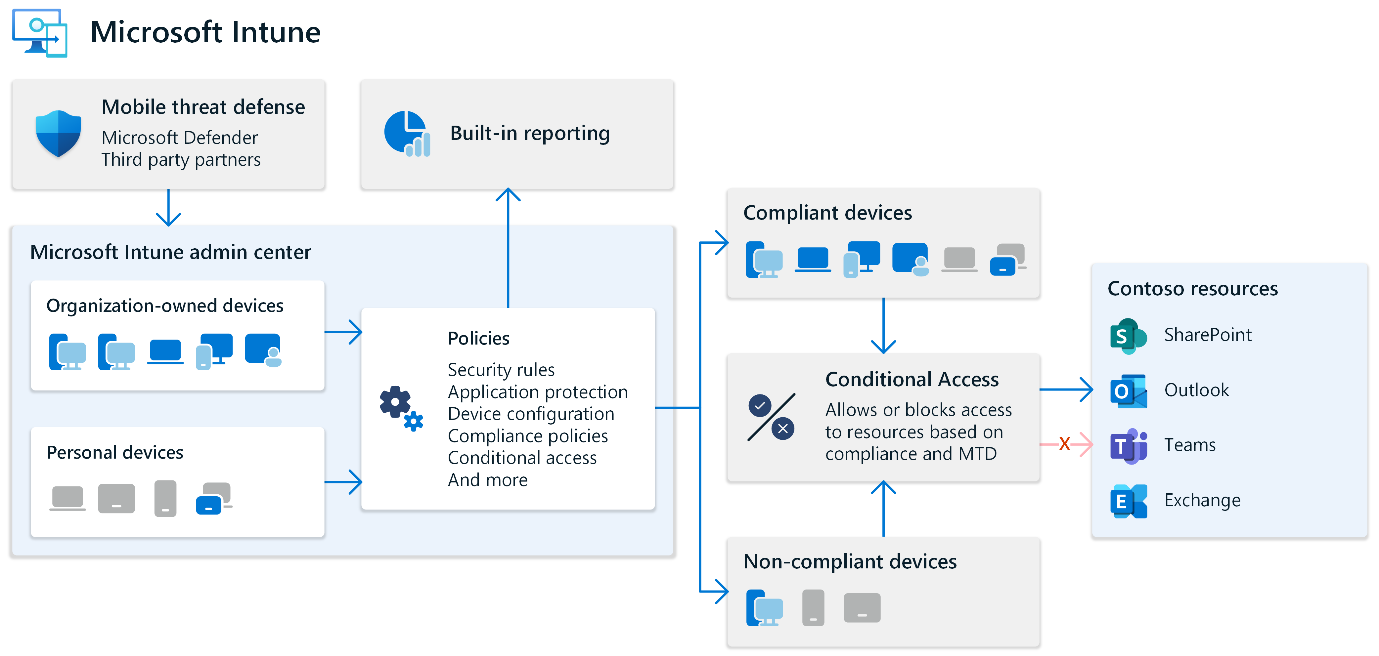
3 Microsoft Intune Essentials – Security & Compliance
Security is a cornerstone of Intune’s value proposition. Integrated with Microsoft Defender for Endpoint, Entra ID (formerly Azure AD) and other Microsoft security services, Intune helps enforce a Zero Trust security model.
It enable…
- Real-time compliance monitoring and conditional access enforcement
- Multi-factor authentication (MFA) and role-based access control (RBAC)
- Data encryption, remote wipe and threat response automation
- Seamless integration with Microsoft 365 security stack
With these capabilities, Intune ensures that only trusted users and compliant devices can access sensitive business data, reducing risk and enhancing resilience.
💡 Do You Know?
Microsoft Intune is all about solving real business challenges that impact productivity, security and cost.
Here is how it helps organizations like yours-
- Still shipping laptops to offices for setup? With Intune and Windows Autopilot, devices can be shipped directly to employees and configured remotely. No IT bottlenecks, no delays, just fast, secure onboarding.
- Concerned about data leaks from personal devices? Intune protects business data at the app level, even on BYOD. Employees can use their own phones, while your sensitive data stays encrypted and controlled.
- Paying for multiple tools to manage devices and apps? If you are already using Microsoft 365 E3 or E5, Intune is included. No need for extra MDM licenses or third-party platforms, cutting costs and simplifying vendor management.
- Struggling to meet compliance across remote teams?Intune enforces security and compliance policies automatically, whether your team is in-office, hybrid, or fully remote. It helps you stay audit-ready without manual effort.
- Lack of visibility into device health and user activity?Intune gives business leaders real-time insights into device status, app usage and security risks, helping you make smarter decisions and reduce downtime.
- Expanding to new regions or hiring globally? Intune scales effortlessly across geographies. No VPNs, no local servers, just secure, cloud-based management that grows with your business.
A unified cloud solution Intune that simplifies device control, secures data and empowers Australian Workplaces to manage hybrid teams efficiently while staying compliant and reducing IT overhead.
Built-In Value – Integrated Security Architecture and Licensing Advantages
One of the most powerful aspects of Microsoft Intune lies in its native integration across Microsoft’s security, identity and endpoint management ecosystem. This deep connectivity enables IT teams to deliver a seamless experience across device provisioning, compliance enforcement and threat protection.
Unified Integration Across Microsoft Services
Intune works in concert with-
- Microsoft Entra ID (formerly Azure Active Directory) for identity and access control
- Microsoft Defender for Endpoint for advanced threat detection and remediation
- Windows Autopilot for automated, zero-touch device provisioning
This tight integration ensures that device onboarding, policy enforcement and security operations are unified under a single cloud-based management framework—streamlining workflows and reducing complexity.
Licensing That Maximizes Value
A major advantage of Intune is its inclusion in Microsoft 365 enterprise licensing. Organizations using Microsoft 365 E3 or E5 plans already have access to Intune Plan 1, eliminating the need to invest in separate mobile device management (MDM) solutions.
This bundled licensing model offers-
- Cost-effective endpoint management without additional licensing fees
- Simplified procurement and deployment processes
- Faster activation of device and security policies across the organization
By leveraging existing Microsoft 365 subscriptions, businesses can unlock enterprise-grade device and application management capabilities, without increasing operational costs.
You can watch the short video below to see how TECHOM Systems supports businesses with Microsoft Intune consulting and deployment, making IT management smoother and more secure.
The fact of Microsoft Intune Adoption
If you are a business owner, decision-maker, or department head wondering why so many companies are switching to Microsoft Intune, this will give you clarity. As businesses adapt to hybrid work, rising security demands and tighter budgets, Microsoft Intune is becoming the preferred choice for modern endpoint management. Its seamless integration with Microsoft 365, cloud-native capabilities and flexible deployment options make it a strategic asset, not just a technical tool. Companies are adopting Intune not just for IT efficiency, but to solve broader operational and compliance challenges.
Key Drivers Behind Intune Adoption
- Cost Efficiency: Intune is included in Microsoft 365 E3/E5 plans, helping businesses eliminate redundant MDM tools and reduce licensing costs.
- Remote Workforce Support: Cloud-based management allows IT teams to configure and secure devices without VPNs or on-prem infrastructure.
- Flexible Modernization: Co-management with Active Directory lets organizations transition gradually without disrupting legacy systems.
- Streamlined Onboarding: Windows Autopilot enables zero-touch provisioning, reducing IT workload and improving employee experience.
- Built-In Compliance: Intune enforces security and regulatory policies across all devices, supporting industries with strict compliance needs.
- Centralized Visibility: Real-time dashboards and reporting help business leaders monitor device health, usage and risk exposure.
Built-In Security and Compliance
Security and compliance are no longer optional—they’re foundational. Microsoft Intune delivers these capabilities as part of its core architecture, helping businesses protect data, enforce access policies and stay audit-ready across all devices and platforms. No bolt-ons, no patchwork—just integrated protection that works from day one.
What Makes Intune a Secure and Compliant Choice
- Unified Policy Enforcement: Apply consistent security baselines across Windows, macOS, iOS and Android devices.
- Conditional Access Integration: Enforce access controls based on user identity, device health, location and risk—powered by Azure AD.
- Threat Detection and Response: Integrated with Microsoft Defender for Endpoint for AI-driven threat detection and automated remediation.
- Data Protection for BYOD: Keep corporate data encrypted and isolated from personal apps on mobile devices.
- Regulatory Compliance Support: Meet standards like GDPR and HIPAA with built-in tools for policy enforcement and reporting.
Why Security-Focused Industries Are Leading the Way
Industries with strict compliance and data protection requirements like finance, healthcare, government and manufacturing, are rapidly adopting Intune as a service is part of their secure digital transformation strategies. These sectors rely on Intune’s deep integration with Microsoft’s ecosystem to enforce policies, protect sensitive data and meet regulatory standards without adding complexity.
Why High-Security Sectors Trust Intune
- Regulatory Alignment: Supports frameworks like HIPAA, NIST, ISO 27001 and more. This makes it easier to meet audit and compliance requirements.
- Identity-Driven Access Control: Azure AD Conditional Access ensures only verified users on compliant devices can access sensitive systems and data.
- Unified Security Stack: Works seamlessly with Microsoft Defender for Endpoint, Teams and Power BI to create a secure, collaborative environment.
- Cross-Platform Protection: Provides consistent security across Windows, macOS, iOS and Android, critical for diverse device environments.
- Data Governance on Mobile: Enforces encryption and app-level data separation to protect corporate information on BYOD devices.
I’ve worked with several organizations to simplify their IT operations by integrating Microsoft Intune into their existing ecosystem. The outcome? Device management becomes part of a seamless, connected workflow instead of a standalone process.
For more insight, have a look at: Top 5 Reasons to Choose Microsoft Intune Expert Services
Implementing Microsoft Intune with a Strategic Approach
Successful Microsoft Intune Deployment goes beyond technical setup. It requires a clear strategy aligned with your organization’s infrastructure, workforce model and compliance needs. While Intune is easy to deploy thanks to its cloud-native design, thoughtful planning ensures long-term scalability and security.
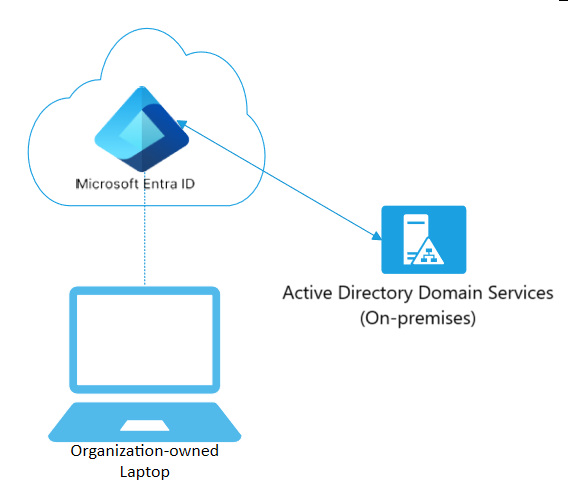
Step 1: Choose the Right Enrollment Model
Decide whether devices will be:
- Azure AD joined – Ideal for Cloud-first environments
- Hybrid Azure AD joined – Suitable for organizations still using on-premises Active Directory
Step 2: Define BYOD vs. Corporate Device Policies
Establish clear boundaries for:
- Corporate-owned devices – full control, compliance enforcement
- BYOD (Bring Your Own Device) – app-level protection, data separation and user privacy
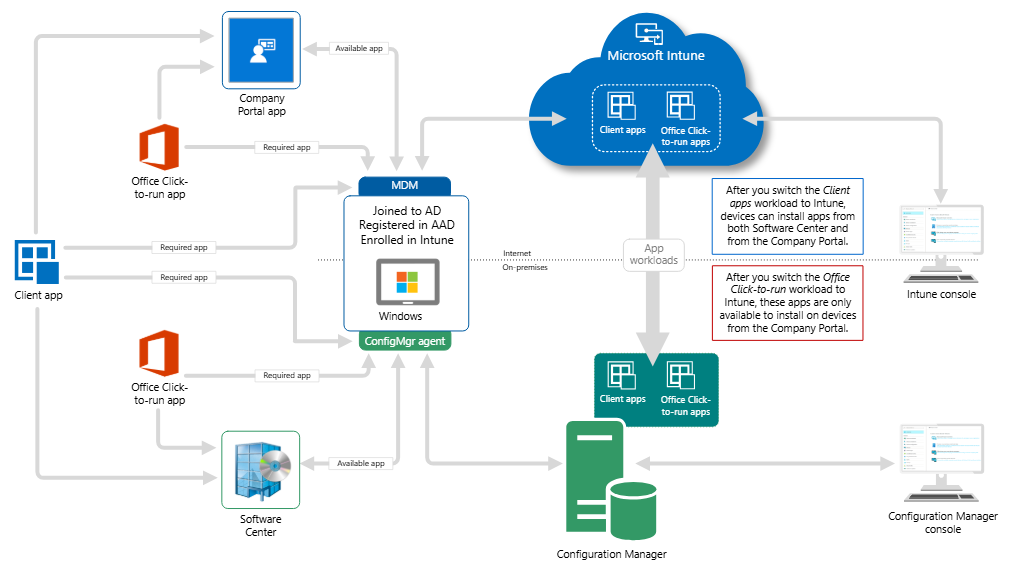
Step 3: Leverage Co-Management with SCCM
For organizations using System Center Configuration Manager (SCCM), Intune supports co-management via Microsoft Endpoint Manager. This allows a phased transition to cloud-based management while maintaining legacy workflows.
Step 4: Plan Intune Policy Configuration
Customize:
- Compliance policies
- Configuration profiles
- App protection rules
Tailor these to match business roles, risk levels and regulatory requirements.

Step 5: Partner with Experts for a Seamless Rollout
Working with a trusted implementation partner like TECHOM Systems ensures your Intune deployment is aligned with Microsoft best practices. From strategy design to policy setup and user onboarding, experts can help organizations like yours in implementing a secure, scalable and future-ready device management framework—without disrupting daily operations.
Explore our Microsoft Intune services and see how TECHOM Systems can help!

Microsoft Intune Superior Capabilities
When we talk about Microsoft Intune Architecture and Essentials, we’re looking at a solution that’s built for the realities of modern work, remote teams, BYOD policies, frontline workers and the need for secure, scalable device management. Intune isn’t just about controlling devices; it’s about empowering IT teams to manage endpoints intelligently and efficiently.
Let’s walk through some of the real capabilities that make Intune stand out-
Cross-Platform Endpoint Management
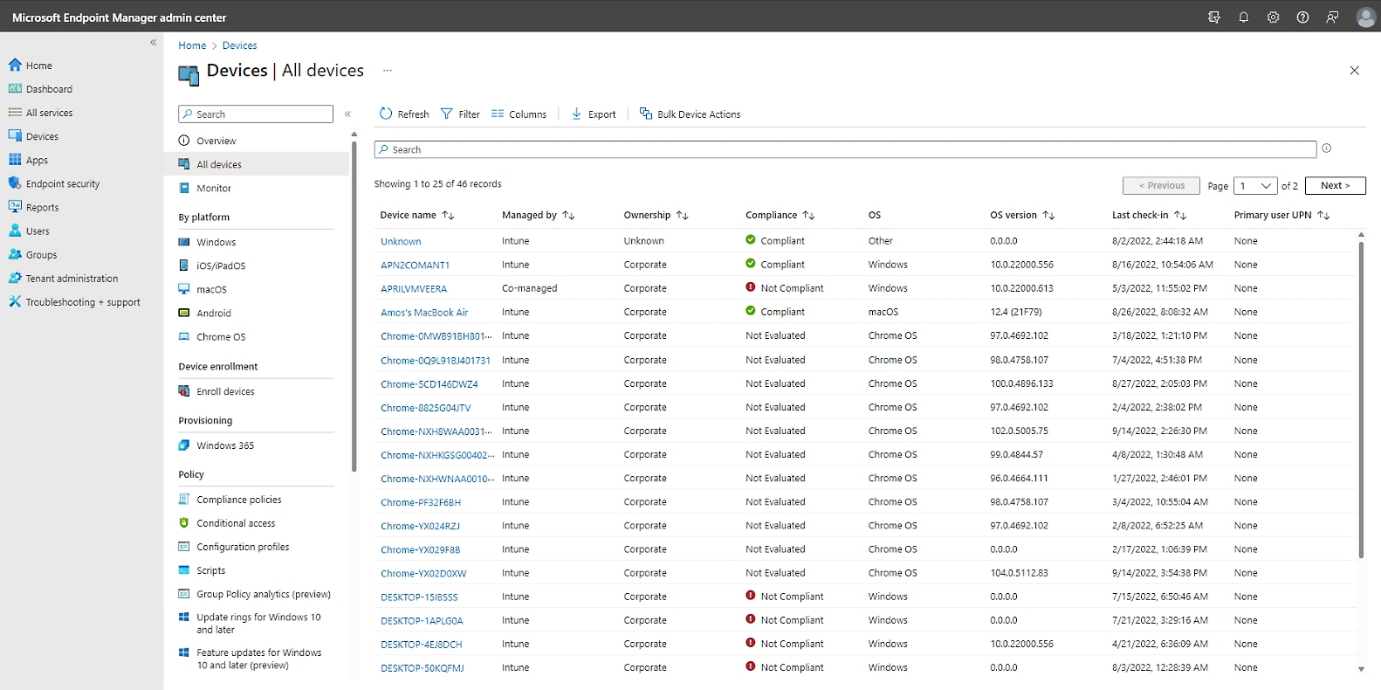
Whether your team uses Windows laptops android phones, iPads, Macs, or even Linux systems, Intune lets you manage them all from one place. That means consistent security policies and simplified administration across your entire organization.
Built-In Endpoint Security
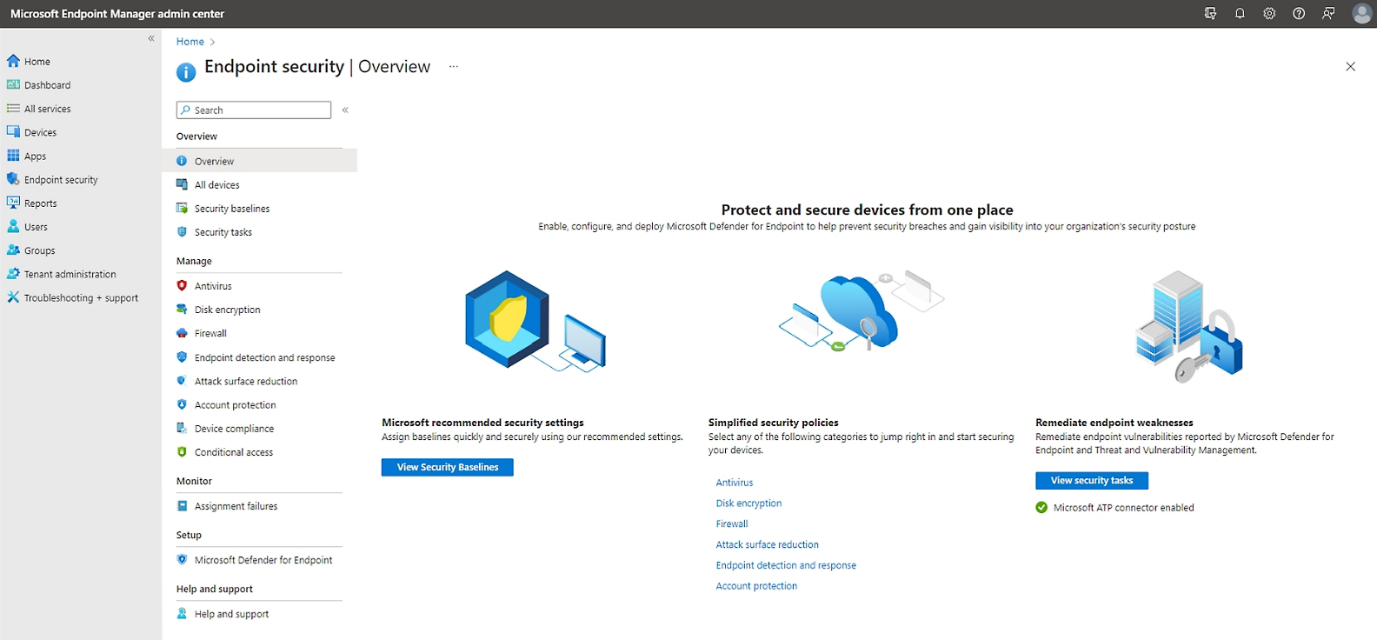
Security is baked into the architecture. With integration to Microsoft Defender, Intune helps enforce antivirus, firewall and encryption policies. You can apply security baselines and monitor threats—all within the same platform.
Mobile Application Management (MAM)
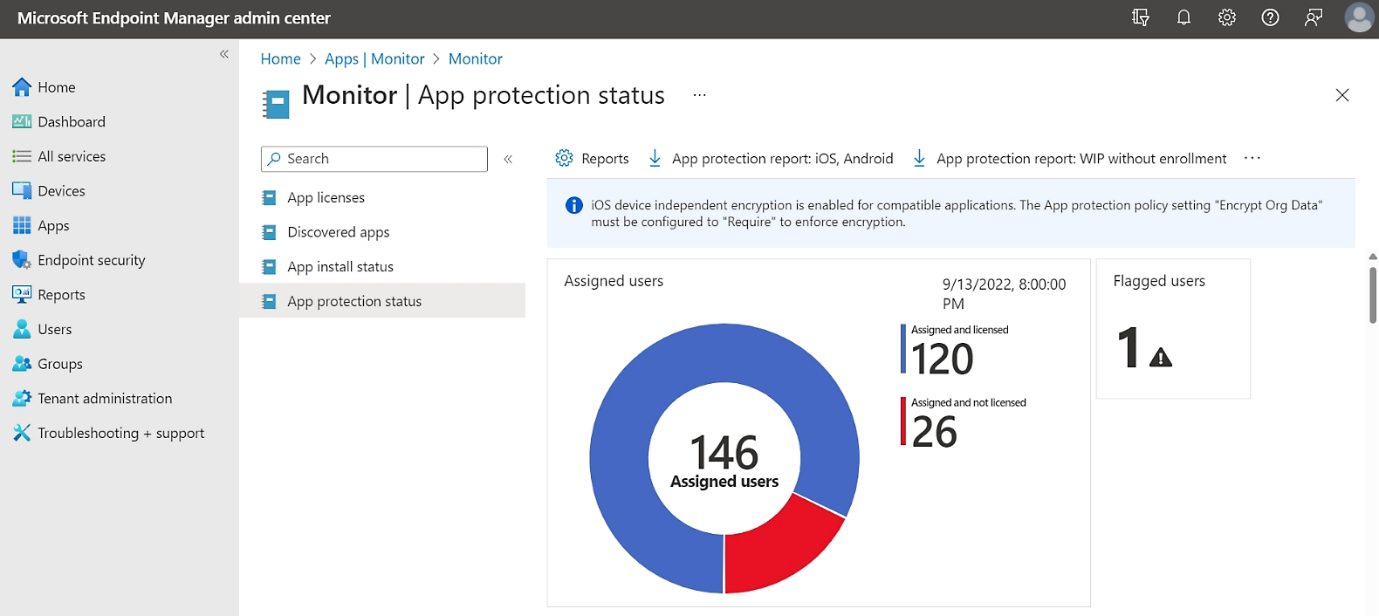
If your business supports BYOD, Intune’s MAM features are a game-changer. You can protect corporate data at the app level, allowing employees to use personal devices for work without compromising privacy or security.
Endpoint Analytics
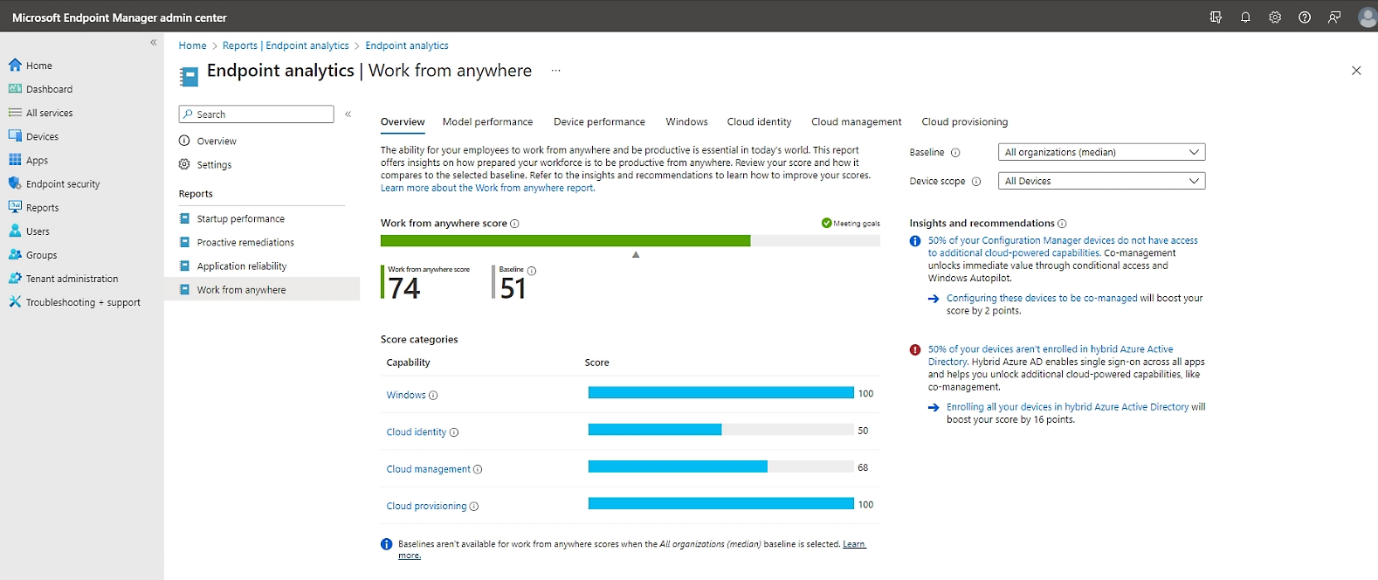
Want to know how your devices are performing or where users are facing issues? Intune’s analytics give you real-time insights into device health, user experience and potential problems, so you can fix things before they escalate.
Specialty and Shared Devices for Frontline Workers
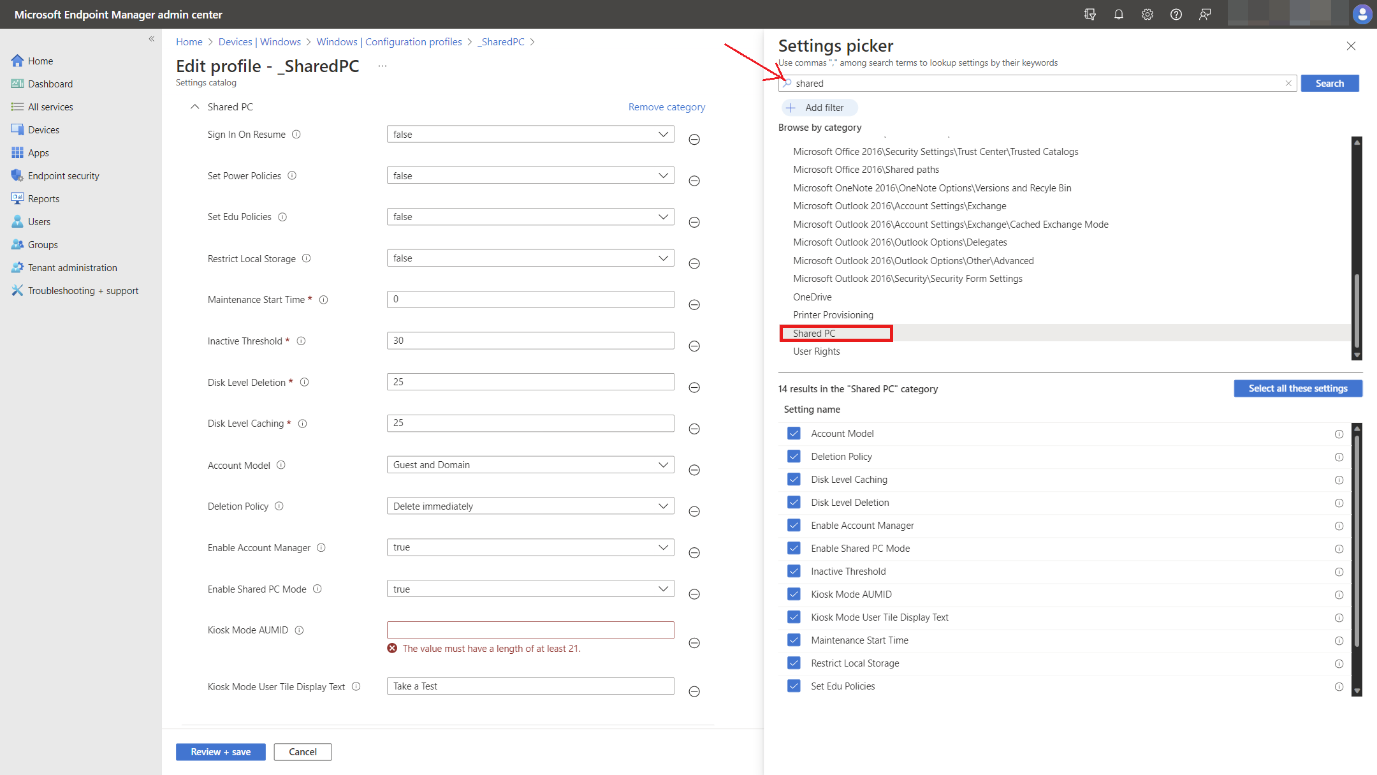
Frontline teams often rely on shared devices or kiosks. Intune makes it easy to configure and secure these setups, ensuring each user gets the right access without compromising performance or data protection.
Real Word Use case
Across industries in Australia, a solid understanding of Microsoft Intune Architecture and Essentials is helping organizations streamline device management, enforce compliance and protect data in hybrid and remote work environments.
- Financial Services: Automates patching, ensures regulatory compliance and maintains tight security controls.
- Nonprofits: Provides centralized device management and secure access for remote and distributed teams.
- Mining & Manufacturing: Simplifies management of thousands of diverse endpoints while integrating with cybersecurity frameworks.
- Healthcare & SMBs: Leverages app-level protection and conditional access to safeguard sensitive data across corporate and personal devices.
- Education: Supports remote learning by managing school-issued devices, securing student data and controlling app access.
- Retail & Hospitality: Ensures consistent device configuration, protects customer data and supports mobile point-of-sale systems.
- Professional Services & Consulting: Enables secure BYOD policies, remote provisioning and policy enforcement across global teams.
- Government & Public Sector: Maintains compliance with strict data security regulations while managing a mix of desktop, mobile and shared devices.
From enabling BYOD programs and supporting remote provisioning to reducing IT overhead, Intune delivers scalable, flexible solutions tailored to the evolving needs of modern Australian workplaces.
💡 What Should I Do Now?
Modern workplaces require agile, secure and scalable IT infrastructure—and that’s exactly what Microsoft Intune Architecture is designed to deliver. Whether you are managing remote teams, navigating compliance requirements, or looking to streamline endpoint operations, now is the time to assess how Intune can support your business goals. Its cloud-native design, mobile device management (MDM) and conditional access capabilities make it a strategic solution for today’s digital-first environments.
- Review Your Current Setup – Evaluate your existing endpoint management strategy. Are your devices secure, compliant and easy to manage across hybrid and remote teams? Identifying gaps in visibility, patching, or access control is the first step toward improvement.
- Start with a Pilot Deployment – Test the core features of Intune Essentials in a controlled environment. A pilot rollout lets you explore MDM, app protection policies and conditional access without disrupting your current systems.
- Align with Business Goals- Ensure your deployment strategy supports broader IT and security objectives. Intune’s flexible architecture allows you to tailor policies for different departments, device types and user roles.
- Get Expert Support- TECHOM Systems offers personalized consultation and deployment planning. We’ll help you design a scalable solution that aligns with your business needs and ensures smooth implementation of Intune’s essentials.
Take the Next Step
Ready to modernize your workplace with Microsoft Intune Architecture and Essentials? Contact us to get started.
About TECHOM Systems
TECHOM Systems supports businesses like yours in modernizing endpoint management and reducing IT complexity. With hands-on experience in deploying and optimizing Microsoft Intune Architecture and Essentials, we work closely with organizations to design scalable, secure and compliant device management solutions. Whether you are starting with a pilot rollout or planning a full-scale deployment, our team ensures a smooth transition with tailored policies, strategic planning and ongoing support. We understand the challenges of hybrid work environments and deliver solutions that align with your operational goals.
Get in touch with us – call 1800 867 669 or email hello@techomsystems.com.au to explore how we can help you build a smarter, safer and more efficient workplace.
Frequently Asked Questions (FAQs)
1. What is Microsoft Intune Architecture and Essentials?
It refers to the core components and design of Microsoft Intune, including Mobile Device Management (MDM), mobile application management (MAM), conditional access and integration with Azure AD, all built to support secure, scalable endpoint management.
2. Can Intune support remote and hybrid work environments?
Yes. Intune is cloud-based and designed to manage devices across locations, making it ideal for remote and hybrid teams.
3. Is Intune suitable for small and mid-sized businesses?
Absolutely. Intune scales easily and offers flexible policy management, making it a great fit for SMBs looking to improve security and reduce IT overhead.
4. How does Intune help with compliance?
Intune allows you to enforce compliance policies, monitor device health and integrate with frameworks like Zero Trust and ASD Essential Eight to meet industry standards.
5. Do I need on-premise infrastructure to use Intune?
No. Microsoft Intune is fully cloud-based, which means you can manage devices and policies without relying on traditional on-premise servers.
Conclusion
Leveraging Microsoft Intune Architecture and Essentials ensures end-to-end support, streamlining deployment, enforcing policies and maximizing the value of your investment so your IT environment remains flexible, resilient and future-ready. Attempting an Intune deployment without expert guidance can leave your organization exposed to security gaps, compliance risks and inefficient workflows. By choosing the best Microsoft Intune consulting and deployment service, your rollout is strategic, fully secure and optimized for productivity.
Contact Us: hello@techomsystems.com.au | 1800 867 669

A results-driven content strategist and IT writer with over 7 years of experience simplifying complex tech concepts into clear, actionable insights. Specialising in cloud computing, cybersecurity, and enterprise IT trends, he crafts content that bridges the gap between technical depth and business value.